Sha1-Hulud: The Second Coming – GitHub Patterns Exposes a Deeper NPM Attack
On 24th Nov 2025, our Internet-scale monitoring systems detected a sharp and anomalous spike in newly indexed Git commits matching highly uniform characteristics. The volume of commits containing the message “Add file” surged from a baseline average of approximately 200/day to more than 13,000 within a single hour. This deviation breached automated anomaly-detection thresholds and initiated an urgent investigation.
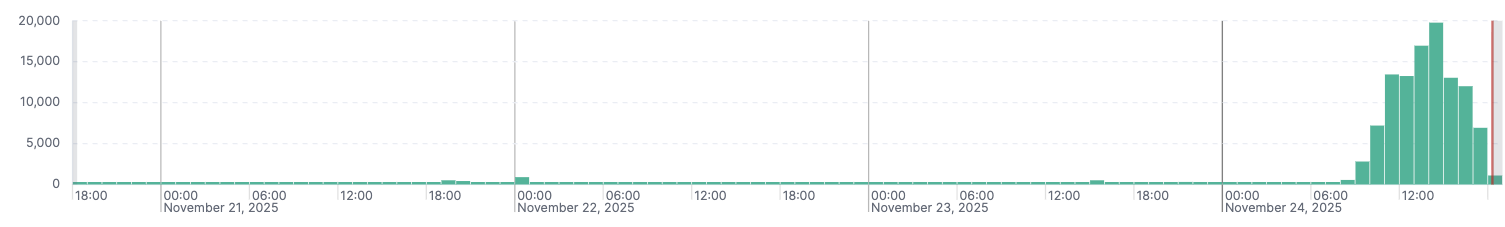
Subsequent analysis confirmed the emergence of a new variant of the Shai-Hulud NPM worm, internally referred to as “Shai-Hulud: The Second Coming.” Unlike typical repository compromise campaigns, this worm targets the NPM ecosystem, infecting user machines and leveraging them as self-hosted GitHub runners. The attacker uses GitHub as a command-and-control (C2) channel to exfiltrate secrets, environment data, and other artifacts from victim machines.
Importantly, the attack does not compromise GitHub repositories directly; instead, it abuses developer endpoints and local development environments.
Detection & Initial Alert
Trigger Event
- Detection system flagged a 65x spike in commits with automated patterns.
- Timeframe: One-hour window.
- Spike initiated within 1 hour of this attack exfiltrating data using Github as C2 channel.
Observed Indicators of Attack
1. Repository Metadata
Affected repositories share an identical and unusual “About” field: “Sha1-Hulud: The Second Coming.”

This tag appears systematically and serves as both an operator signature and a cluster identifier for correlating impacted repos.
2. Commit Message Patterns
Automated commit messages follow a narrow, repetitive format:
- “Add file”
- “Add Discusion” (with the consistent misspelling)
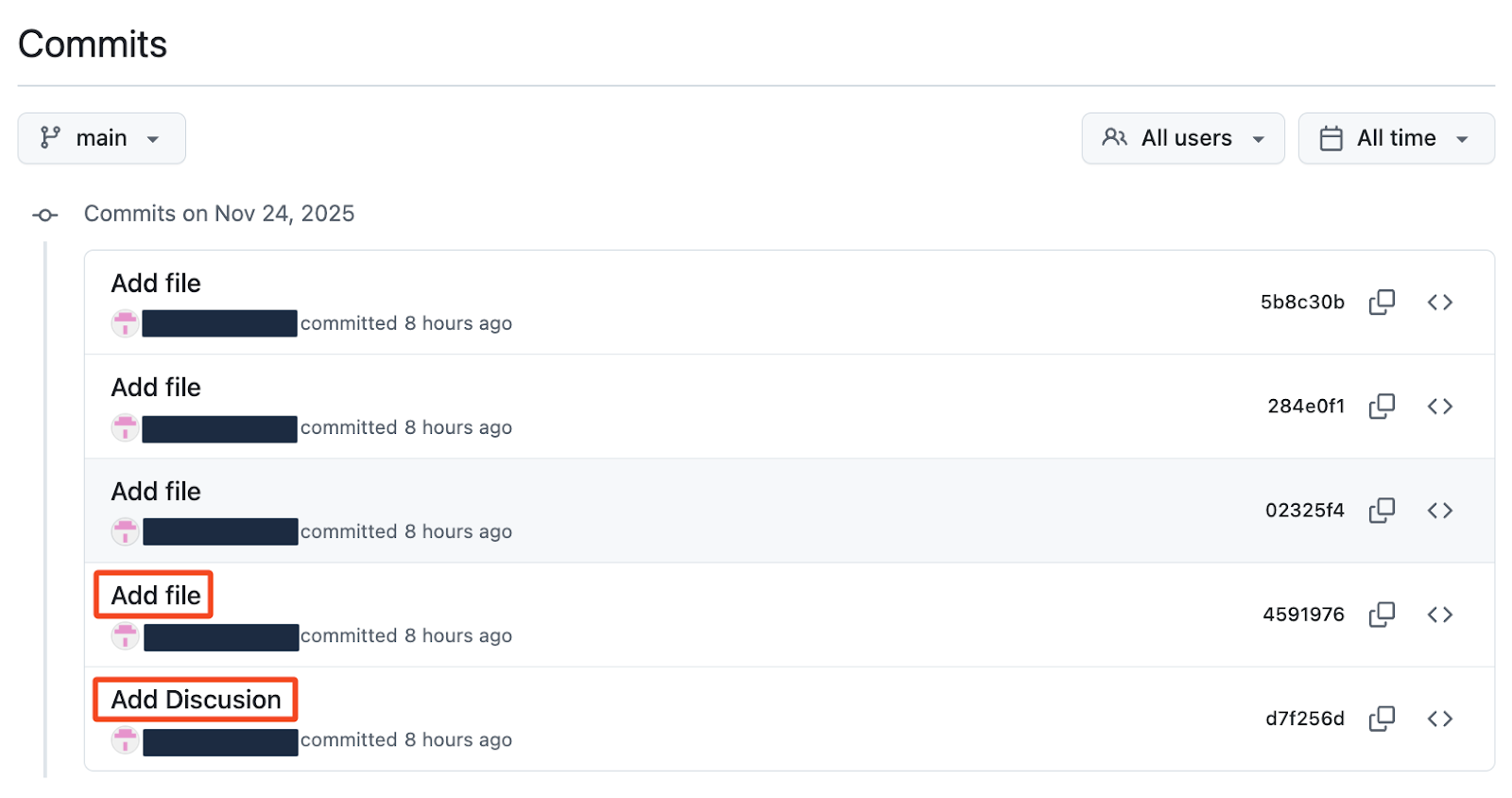
The uniformity suggests scripted mass-repo deployment by the worm.
Kill Chain Summary
Although analysis is ongoing, early reverse-engineering shows:
- Machine compromise via malicious NPM package
- Infects local workstation.
- Local host pivoted into self-hosted GitHub runner
- Executes attacker workflows on the victim machine.
- GitHub used as C2
- Worm pulls tasks, secrets, environment configs, and telemetry artifacts from GitHub infrastructure.
- Creation of attacker-controlled repos
- Automated commit propagation across newly created repositories.
- Tagging repos with “Sha1-Hulud: The Second Coming.”
- Likely for clustering and operator visibility.
Early Onset Repositories
The campaign appears to have begun roughly 12 hours ago, coinciding with our initial alert about unusual GitHub commit activity.

Users impacted in the earliest observable wave include:
- allganize-junryeol
- Jyejin
- 0816i
- TakuyaSugitani
- (along with many other accounts generating randomized repository names)
These repositories were created within minutes of the initial spike, marking them as part of the campaign’s first wave.
These two GitHub profiles (were among the first ones) displayed unusually dense clusters of malicious repositories:
1. Jyejin

- Total repositories: ~80
- Attack-linked repositories: ~55
- Exhibits rapid automated repo creation over a tight time interval.
2. TakuyaSugitani
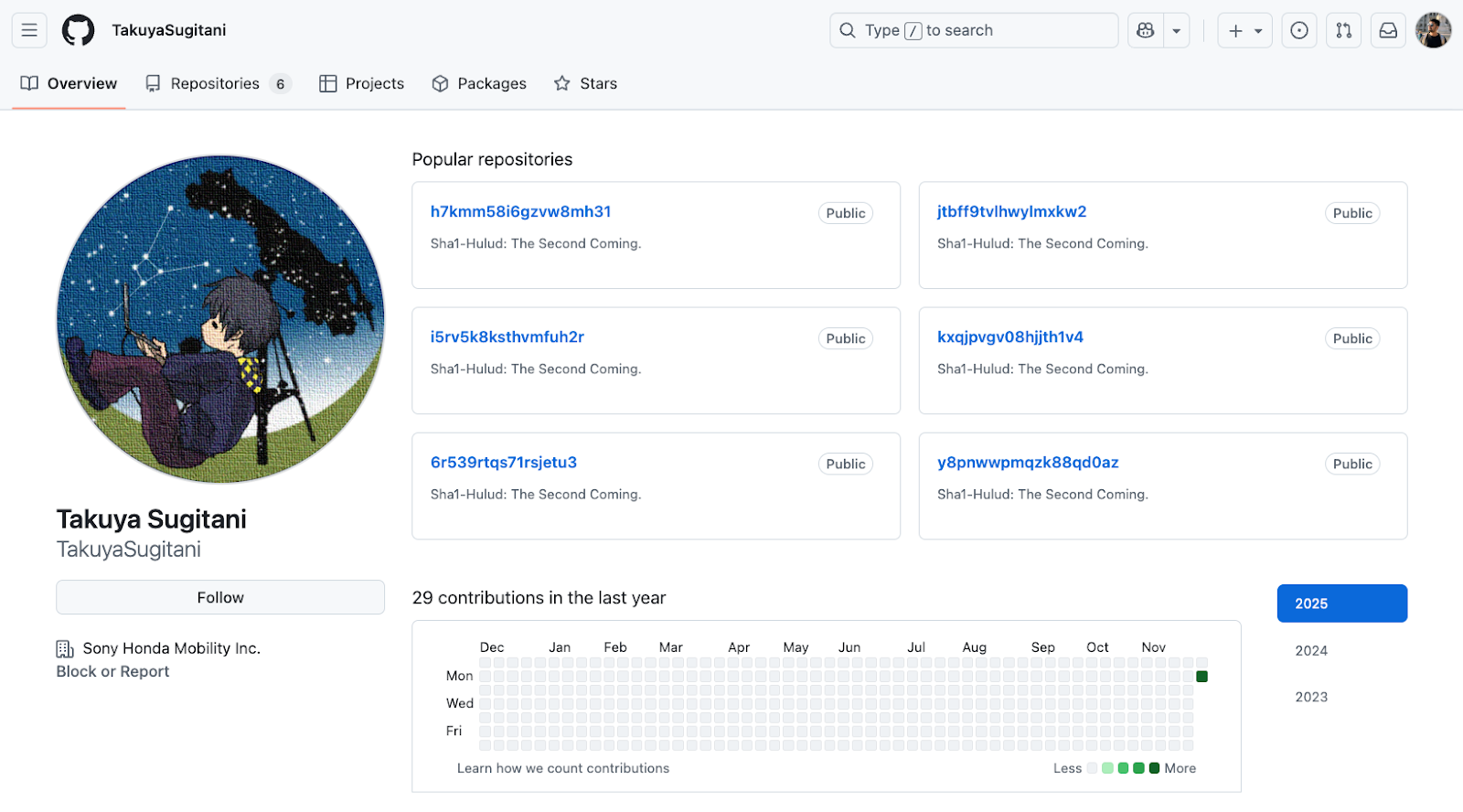
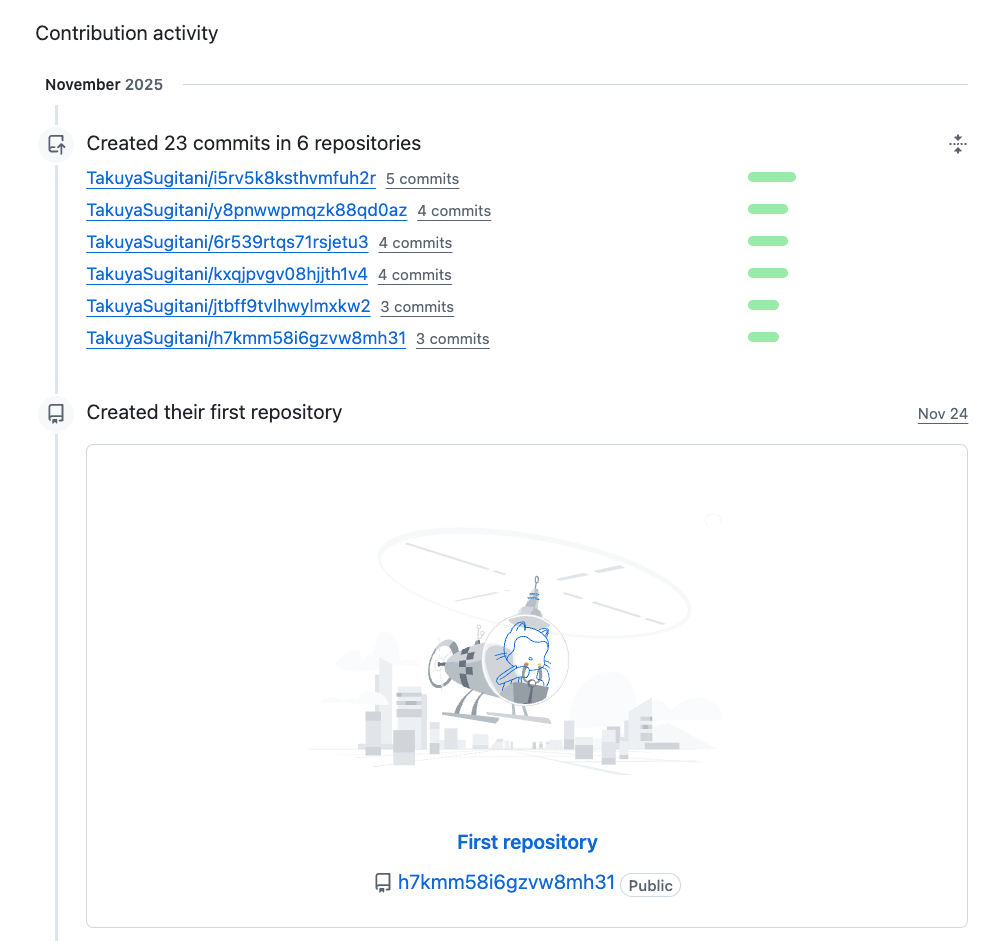
- The account consists exclusively of repositories associated with the attack.
- No benign or historical activity visible.
- Likely used as a seeded operator node or automated bot account.
These accounts are important pivot points for tracking the spread and understanding attacker infrastructure.
What Should You Do?
What is affected?
- Local developer machines via malicious NPM packages.
- GitHub user workflows via abuse of the self-hosted runner model.
- Secrets, environment values, tokens that can be exfiltrated through workflow execution.
If you use NPM or GitHub in your workflow, take a few quick actions to stay safe:
- Check Your Recent NPM Installs – If you installed any new packages in the last 24–48 hours, review them. Delete anything that looks suspicious or unnecessary.
- Rotate All Secrets – Refresh GitHub tokens, CI/CD secrets, cloud keys, and environment variables. Assume anything on a potentially affected machine may be exposed.
- Inspect Your GitHub Account Activity – Look for:
- unknown repositories
- unexpected commits
- new self-hosted runners
- unusual access tokens or OAuth authorizations
- Run a System Scan – If your machine builds or installs NPM packages, run a malware/behavioral scan to rule out post-install scripts.
- Rebuild CI Environments – If you use ephemeral CI runners, recreate them. If you use persistent ones, audit them thoroughly.
- Enable Protective Controls – Turn on 2FA, restrict token scopes, and enforce least-privilege access for CI/CD secrets.
- Follow NPM and GitHub Advisories – These campaigns evolve quickly. Stay updated and patch fast.
Preliminary Conclusions
The activity represents a scaled and automated follow-up to the earlier Shai-Hulud supply chain incident.
Key takeaways:
- This is an NPM ecosystem infection acting as a GitHub workflow worm.
- The worm is designed for exfiltration, staging, and distributed GitHub-mediated C2.
- Automated repository creation is used for stealth, obfuscation, and volume-based distraction.
RedHunt Labs is continuously monitoring our customers for any exposures related to the “SHA1-HULUD: The Second Coming” attack and working with them to mitigate the risk. Our Continuous Threat Exposure Management (CTEM) platform goes a step further by continuously monitoring for exposures across your entire attack surface, helping you prioritize what really matters and take precise action before attackers do.
Book a scan 🔗 and learn more about how RedHunt Labs can strengthen your exposure management.

