Continuous Threat Exposure Management (CTEM), Explained: What It Is and How RedHunt Labs’ Platform Enables It
As organizations expand their digital footprint, their external attack surface becomes increasingly complex. Threats evolve faster than scheduled scans can catch them, and digital infrastructure now changes hourly, not quarterly. Traditional security operations, often reactive and siloed, struggle to keep up. That’s where Continuous Threat Exposure Management (CTEM) comes in. It emerged as a strategic framework that brings structure, visibility, and validation to modern exposure management.
In this blog, we’ll break down what CTEM actually means, how it helps security teams stop chasing shadows, and how RedHunt Labs’ Platform fits into the CTEM lifecycle.
First Things First: What is CTEM?
Coined by Gartner in 2022, Continuous Threat Exposure Management is a structured approach that enables organizations to continually identify, validate, and mitigate exposures before attackers can exploit them.
CTEM is not a tool. It’s a cyclical, continuous process designed to help security teams move from asset visibility to exposure prioritization and action. It consists of five continuous, connected stages: Scoping, Discovery, Prioritization, Validation, and Mobilization.
This allows security leaders to assess how exploitable their real-world environment is, how prepared their teams are to respond, and where they should invest next.
Why Traditional Approaches Fall Short
Let’s face it. Most organizations still rely on some combination of:
- Periodic vulnerability scans
- Annual pentesting/red teaming
- Static asset inventories
The problem? None of these is continuous. They give snapshots in time. CTEM is different; it fills the gap between reactive detection and proactive defense. It recognizes that exposures are dynamic, not static. It’s not enough to know where you stood last month. You need to know what’s changing right now.
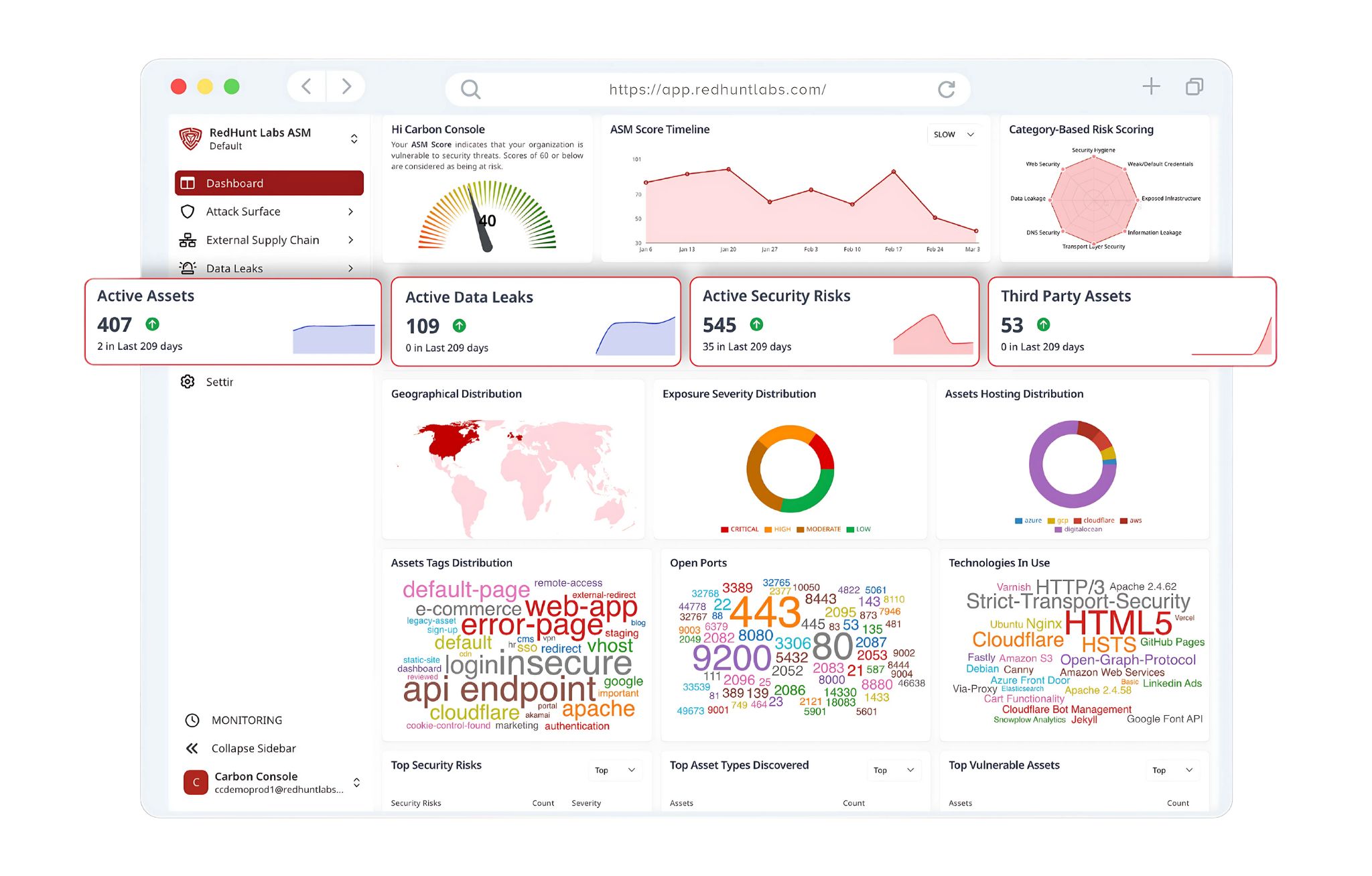
RedHunt Labs Platform: That Powers Up CTEM Lifecycle
You can’t implement CTEM in a slide deck. You need tooling that supports each phase without creating more work. This is where RedHunt Labs’ Platform comes in.
Let’s map each CTEM stage to what our platform does in practice:
Phase 1: Scoping – Define What to Evaluate
Scoping sets the boundaries for what will be evaluated in each CTEM cycle. This includes identifying domains, IPs, subdomains, web and mobile apps, cloud-hosted assets, third-party SaaS tools, APIs, etc.
CISOs should ensure that asset discovery efforts extend across business units, subsidiaries, and supply chain integrations, not just managed IP ranges. Visibility must be established across both managed and unmanaged environments.
RedHunt Labs Platform provides:
- Domain, IP, and subdomain enumeration
- Discovery of mobile and web-facing applications
- GitHub and code repository leak detection
- Shadow IT & Shadow SaaS discovery
- Subsidiary & third-party asset mapping, and more.
“For many organizations, 30-40% of internet-facing assets are unknown to internal teams. An updated scoping strategy must go beyond spreadsheets and CMDBs.” – Gartner, CTEM Framework, 2022.
Phase 2: Discovery – Identify Real Exposures
Once the scope is established, discovery is about continuously identifying exposures, not just collecting inventory. This includes detecting misconfigurations, leaked credentials, login pages, exposed development infrastructure, and security risks.
CISOs should treat this phase as the baseline for all subsequent metrics. Continuous scanning, with both passive and active techniques, is critical for real-time visibility.
How RedHunt Labs Platform enables this:
- Continuous passive + active recon
- Deep metadata enrichment (tech stack, headers, SSL, page titles, etc.)
- Detection of misconfigurations, leaked secrets, and exposed APIs
- Asset change tracking (appearance/disappearance of services)
- Security risk discovery
A few examples of such real-world threats we surface:
- S3 buckets with PII
- Exposed admin panels
- Forgotten third-party services
- Subdomain takeovers and more…
Continuous visibility is not just about finding new assets; it’s about detecting when something quietly changes. Discovery must run as a persistent service, not a quarterly audit.
“Threat actors often gain initial access by exploiting unknown and unmanaged assets that aren’t part of the organization’s known perimeter.” – CISA, Shadow IT Advisory, 2023
Phase 3: Prioritization – Know What Matters Most
Not all exposures are equal. Prioritization is where CTEM starts to reduce noise, surfacing the threats that are both exploitable and business-relevant. Security leaders should ensure prioritization incorporates asset sensitivity, exploitability, business impact, and not just CVSS.
How RedHunt Labs Platform supports this:
- Category-Based Risk Scoring
- Asset classification and enrichment
- Exposure severity scores based on exploitability
- Asset importance scoring
- Tagging by environment, team, and business function
Risk scoring should evolve beyond vulnerability type to exposure type, business impact, and exploit maturity.
“80% of breaches involve assets that had known issues, but teams failed to prioritize or respond in time.” – Verizon DBIR, 2023
Phase 4: Validation – Confirm If Exploitable
This is the phase where theoretical risk becomes real. Exposures must be validated, ideally with proof-of-concept, known exploits, or testing, to ensure teams are not chasing false positives. CISOs should guide validation toward attacker-centric logic: if an exposure is visible, exploitable, and connected to sensitive systems, it deserves priority.
How RedHunt Labs supports this:
- Exploit-aware tagging (e.g., latest CVEs, changes in CVEs, CVEs under active exploitation)
- Pentest integration & exploit validation support
- Integration with vulnerability research, enrichment feeds, and contextual detection logic
Exposure validation bridges the gap between visibility and action and determines how much of your backlog is a real risk.
“Organizations that perform regular exposure validation reduce false positives by 38%, freeing up resources for actual response.” – Forrester, External Exposure Study, 2023
Phase 5: Mobilization – Assign the Right Fix to the Right Team
Finally, the findings must be translated into action. Mobilization ensures the exposure is routed to the right team with enough context to respond quickly. Security leaders should focus on operationalizing handoffs so that the response doesn’t stall due to ownership gaps.
RedHunt Labs enables this with:
- Asset-to-owner resolution (teams, business units)
- Automated ticketing integrations (Jira, ServiceNow, etc.)
- Attack Surface Reduction feature
- Exposure timelines and resolution tracking
- Alerting tied to risk score and asset classification
- Custom alerting and notification recipes
An exposure is only closed once it’s remediated. The speed of that closure is often determined by the clarity of ownership.
“Only 54% of security findings in enterprises are actually remediated, and most lack ownership assignment or follow-up tracking.” – ESG Research, 2023
Why This Matters Now
The attack surface is growing faster than most teams can manage. Continuous visibility, especially into SaaS, third parties, and shadow assets, is no longer optional. CTEM is gaining traction as the operating model for modern exposure management. Security leaders increasingly want measurable risk reduction instead of abstract compliance checklists. CTEM enables:
- Measurable outcomes (MTTR, MTE, discovery coverage)
- Repeatable cycles for continuous improvement
- Business-context prioritization over vulnerability count

In a Nutshell: RedHunt Labs’ Platform Makes CTEM Achievable
CTEM isn’t about perfection. It’s about momentum. It’s a way to continuously reduce risk in a world where things change faster than old-school tools can keep up.
With RedHunt Labs Platform, your security team can:
- Discover what’s exposed – externally, in the cloud, or via vendors
- Validate exposures before attackers do
- Prioritize by business impact
- Close the loop with faster remediation guidance
Additionally, our platform offers unique capabilities not commonly found in traditional ASM tools:
- SaaS risk discovery from passive telemetry
- Subsidiary & third-party exposure correlation
- Risk scoring by exposure category
- Attack Surface reduction and risk advisor
- Pentesting and additional validation support
CTEM isn’t a future ideal. You can start now, with the right structure and the right platform. If ASM is your foundation, CTEM is the mission. And RedHunt Labs helps you operationalize both.

Final Word: CTEM is How Security Moves Forward
We’re moving past the era of once-a-year pentesting and quarterly patch reviews. Today’s threat landscape demands a faster, smarter approach. CTEM gives you the mindset, and RedHunt Labs Platform gives you the muscle. Whether you’re benchmarking your CTEM maturity or starting your first external risk initiative, our EASM gives you the full-spectrum visibility and validation foundation that CTEM demands.
Book a demo and see how exposure management feels when it’s continuous, connected, and finally under control.

