E-commerce Fraud-as-a-Service: How Scammers Exploit Brand Trust at Scale
In the rapidly evolving digital marketplace, e-commerce brands have become prime targets for cybercriminals. Beyond traditional data breaches, these brands now face sophisticated scams that exploit their reputation, deceive consumers, and erode trust.
Drawing from investigations conducted by RedHunt Labs’ threat intelligence team, this blog delves into some of the most prevalent scams targeting e-commerce platforms and highlights how a Digital Risk Protection (DRP) solution can help fortify your brand against these threats.
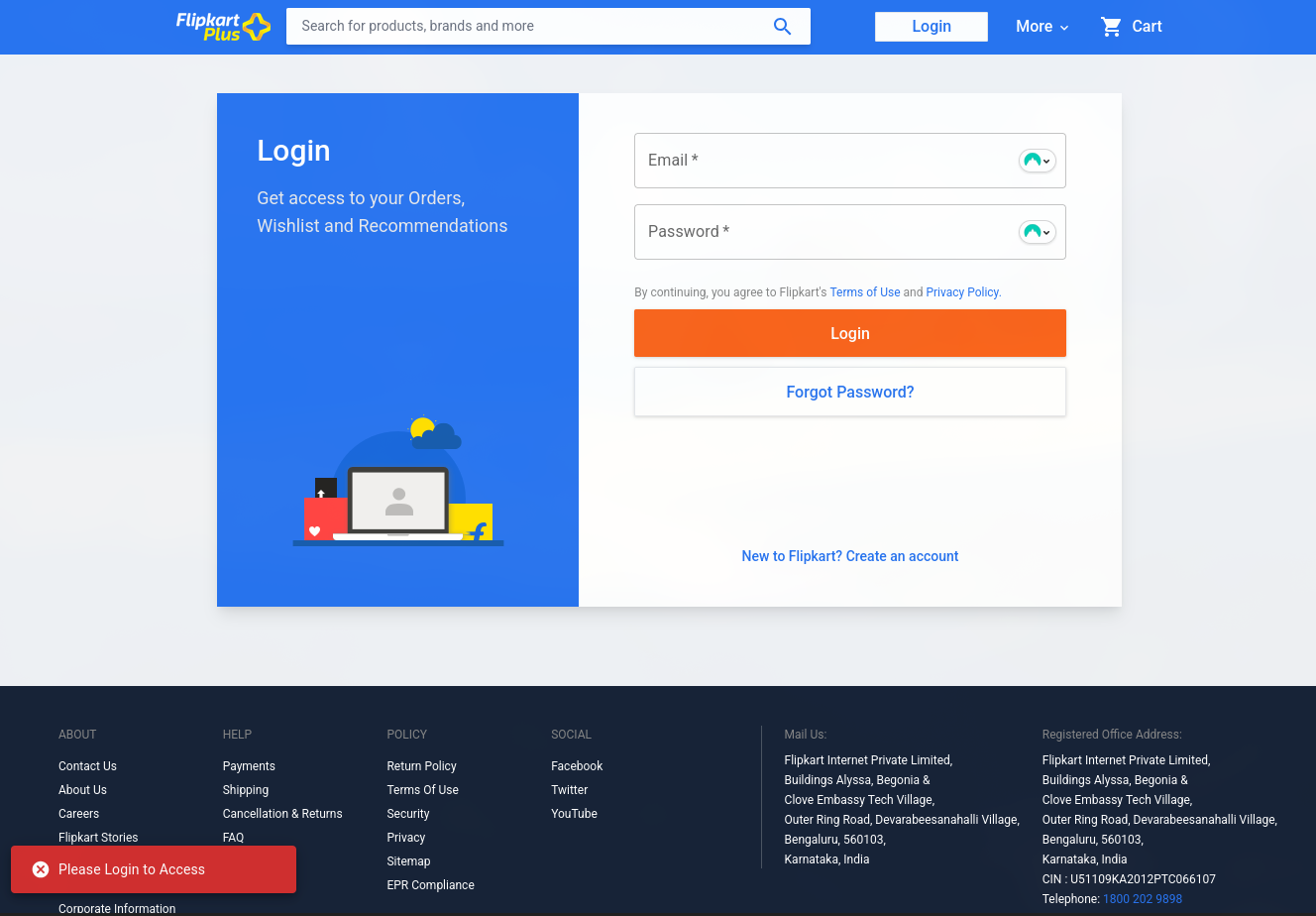
1. Credential Phishing via Deceptive Login Pages
Our threat intelligence team has observed that as cybercriminal tactics evolve, phishing is no longer confined to emails or shady links. A new wave of scams involves deceptive login pages that mirror trusted e-commerce platforms, especially during seasonal sales and high-traffic periods.
These phishing kits are often bundled and sold as part of Phishing-as-a-Service (PhaaS) ecosystems, enabling low-effort credential theft at scale.
Cybercriminals are actively deploying fake login pages that mimic legitimate e-commerce platforms with alarming precision. These pages are crafted to deceive users into entering their credentials.
Critically, they are increasingly being promoted through paid advertisements on platforms like Facebook and Instagram. This marks a significant shift – phishing isn’t just hiding in spam emails anymore, it’s now part of visible, widespread ad campaigns.
How These Phishing Sites Spread
These credential phishing pages are:
- Promoted via Facebook and Instagram ads with fake offers or login prompts.
- Embedded in scam websites mimicking real e-commerce portals.
- Spread using URL shorteners or redirects to obscure their true destination.
Examples Identified:
- hxxps://atit[.]org[.]in/login
- hxxps://gostore[.]app/flipkart/login?from=account
- hxxps://ecom-amazon-react-app[.]vercel[.]app/
- hxxps://amazon-login-page[.]webflow[.]io/
These phishing campaigns are often powered by Phishing-as-a-Service (PhaaS) operations.
What is PhaaS?
PhaaS (Phishing-as-a-Service) is a growing underground economy where threat actors sell or rent phishing kits and infrastructure to others. These services allow even non-technical actors to:
- Generate cloned login pages.
- Bypass CAPTCHA and MFA.
- Validate credentials in real-time.
- Monitor victims through admin dashboards.
In essence, PhaaS transforms phishing into a scalable, subscription-based service model.

2. Fraudulent E-Commerce Storefronts
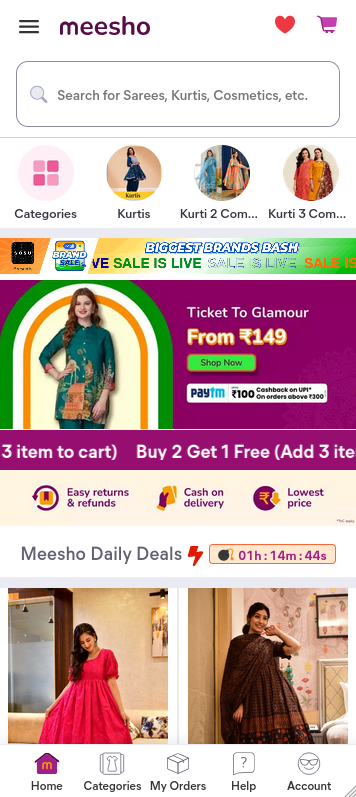
Our threat intelligence team has identified a significant trend where, beyond login credentials, scammers are building full-fledged eCommerce websites that mimic real shopping portals. These scam sites promise unrealistic deals and aim to steal user data and money.
While they don’t collect passwords, they harvest names, addresses, and payment details – qualifying them as a form of phishing.
Fake eCommerce websites do more than defraud users – they directly undermine the trust and brand value built by legitimate online platforms. These scams are designed to look authentic and are aggressively promoted through Facebook and Instagram advertisements, making them appear credible to the average shopper.
How These Scam Sites Operate
Fraudulent sites typically:
- Advertise unbelievable deals like dresses for under ₹100 or wireless earbuds for ₹500.
- Collect sensitive user information such as name, phone number, and delivery address.
- Accept payments via popular and easy methods like UPI, increasing user trust.
Example scam store links:
- hxxps://offer[.]win-dhamaka[.]live/Bdh/OFFER/earphone/
- hxxps://offer[.]win-dhamaka[.]live/ve3/OFFER/fk99/
- hxxps://shop[.]offerindia[.]xyz/dvtbt/OFFER/meesho/
Despite not stealing credentials, these scams fall under phishing, as they harvest personal and payment-related data under false pretenses.
Infrastructure and Distribution
- These campaigns are hosted on disposable or suspicious redirector domains such as biogame.live, which is commonly seen in scam site networks.
- Most of these scams are targeted exclusively at mobile users and will not function or render properly on desktop browsers. This is an intentional tactic to bypass detection – the mobile payment flow appears smooth and legitimate.
- While the sites appear to integrate with real payment gateways, they often redirect users directly to UPI apps like Google Pay or PhonePe, without any actual transaction backend.
- Many of these scam pages share identical templates, payment flows, and ad creatives, suggesting the use of a scam-as-a-service kit.
- Campaigns are often timed around sales seasons and distributed rapidly via paid ads to scale reach before takedown. such as biogame.live, which is commonly seen in scam site networks.
- Many of these scam pages share identical templates, payment flows, and ad creatives, suggesting the use of a scam-as-a-service kit.

3. Deceptive Hiring Campaigns Exploiting Brand Names
Furthermore, our threat intelligence team has discovered that E-commerce brands are also exploited through job-related scams, especially targeting users in low-income groups. These scams come in two forms: fake work-from-home roles (like packing or delivery) and fraudulent earning apps that claim to offer commissions or passive income. Distributed via Facebook groups, Telegram, and YouTube, these schemes misuse brand names and visual assets to gain trust.
Scammers are also exploiting e-commerce brands by launching fake hiring and work-from-home scams. These scams typically fall into two categories:
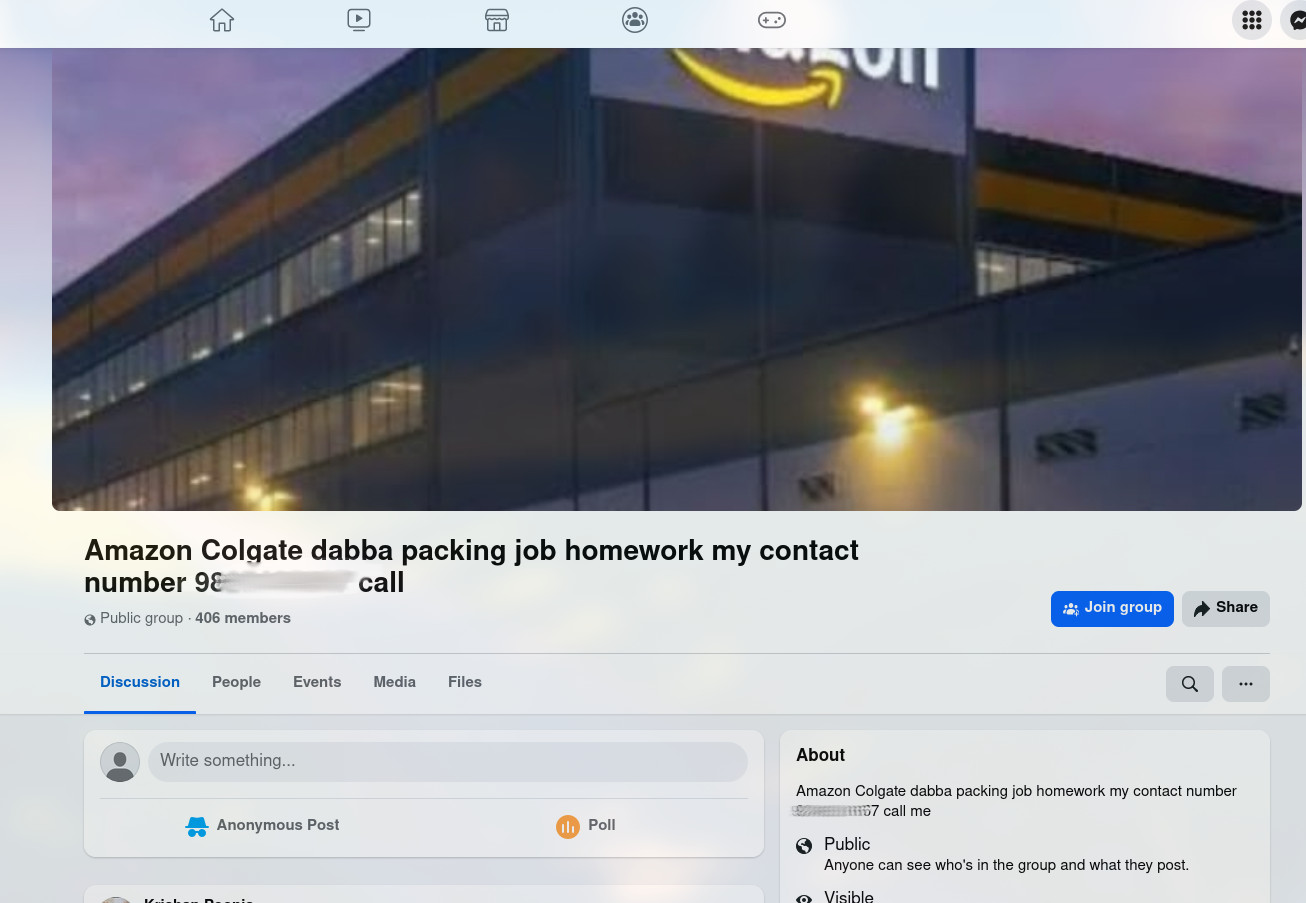
1. Part-Time Job Scams (Packing/Delivery Work)
Promoted heavily in Facebook groups and pages, these scams claim to offer home-based roles such as:
- Pencil packing
- Delivery packaging
- Product labeling

Victims are lured with promises of attractive salaries and advance payments. In reality, they are:
- Asked to pay upfront fees for job registration or training materials.
- Ghosted after payment or sent fake onboarding details.
These pages often use phrases like:
- “Amazon company Home wark job pencil packing 30000 salary 15000 advance kam”
- “Amazon Pen Pencil Packing Job”
Some even include phone numbers directly in the group or page title to attract direct messages.
Example Facebook groups/pages:
- https://www.facebook[.]com/groups/697523674673739/
- https://www.facebook[.]com/groups/528851798693108/
- https://www.facebook[.]com/groups/696260264841188/
These scams largely target housewives, students, and people seeking part-time remote work, taking advantage of job insecurity and the popularity of e-commerce platforms.
2. Fake Earning & Investment Apps
Another variation involves scam apps and websites claiming to be investment platforms or income-generating services tied to e-commerce brands. These scams are often promoted through Telegram channels and YouTube videos, where scammers share referral links and misleading testimonials.
These sites typically:
- Claim to offer daily commissions or cashback earnings
- Require an initial deposit or “activation fee”
- Disappear or lock users out once funds are transferred
Example site:
- hxxps://ama-asia[.]xyz/h5/#/pages/login/login
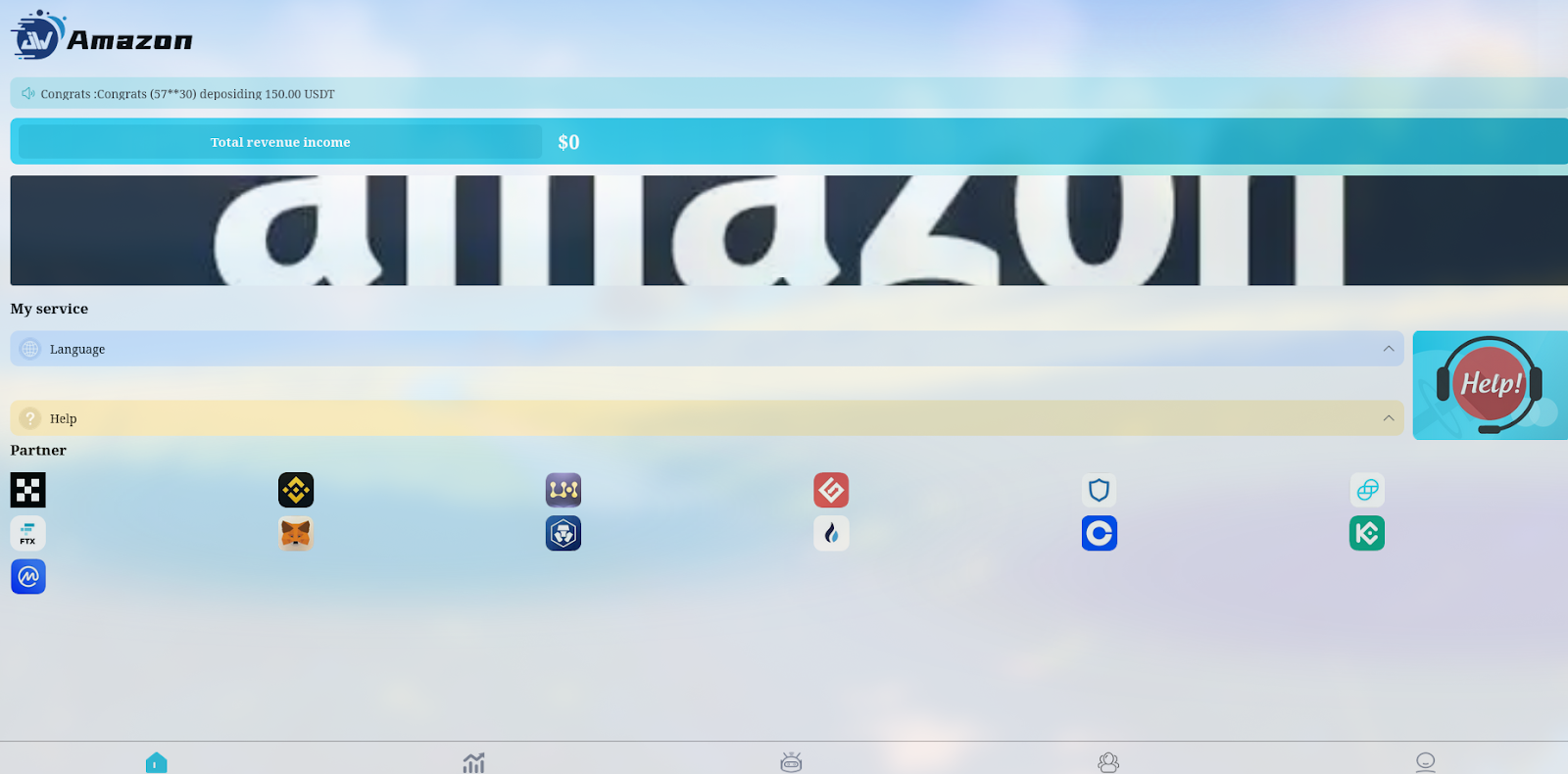
These scams create a false impression of brand affiliation through logos, fake testimonials, and cloned UI designs
The Repercussions: Beyond Immediate Financial Loss
The impact of these scams extends beyond the immediate victims:
- Brand Reputation Damage: Association with scams can erode customer trust and loyalty.
- Legal and Compliance Risks: Failure to address such threats may lead to regulatory penalties.
- Operational Disruptions: Resources diverted to manage fallout from scams can hinder business operations.
Immediate Steps Your Brand Can Take
While advanced protection requires specialized solutions, there are a few quick, actionable steps you can take today to reduce risk and protect your customers — at zero cost:
1. Educate Your Customers:
Use social media posts and website banners to remind users to only shop on your official domain and avoid third-party links sent via messages or ads.
2. Set Up Basic Monitoring:
Create free Google Alerts for your brand name paired with words like “scam,” “fraud,” or “giveaway.” This helps you spot potential impersonation campaigns early.
3. Report and Document Scams Promptly:
Encourage your customer support team to collect evidence of reported scams, such as screenshots or URLs, and report them to the relevant ad platforms or authorities.
How RedHunt Labs Fortifies Your Brand Against Scams
RedHunt Labs offers a holistic Digital Risk Protection (DRP) framework to detect and respond to e-commerce brand scams at scale. Our approach includes:
1. Proactive Threat Detection
- Monitoring ad platforms and social channels for scam promotions
- Detecting fraudulent websites, phishing pages, and fake job listings
2. Infrastructure Intelligence
- Identifying parked and typosquatting domains
- Uncovering reused phishing kits and hosting infrastructures
- Mapping scam networks and scam-as-a-service patterns
3. Social and Platform Surveillance
- Tracking Telegram and YouTube campaigns tied to fake earning apps
- Detecting impersonation in Facebook groups, pages, and scam forms
- Using sock puppet personas to infiltrate fraud rings for early intelligence
4. Response and Enforcement
- Supporting domain takedown and removal of malicious ad content
- Providing evidence packs for legal escalations and brand protection
This consolidated DRP approach enables brands to safeguard their reputation, reduce consumer-targeted fraud, and stay ahead of cybercriminal campaigns.
Conclusion
As cybercriminals turn your brand’s hard-won trust into their primary weapon, the question is no longer if you will be targeted, but how prepared you will be when it happens. Proactive digital risk protection is the only way to ensure your brand’s integrity and maintain customer loyalty in an increasingly hostile digital landscape.
And if you are thinking about security at scale, that is exactly where RedHunt Labs comes in. Our Continuous Threat Exposure Management (CTEM) platform goes a step further by continuously monitoring for exposures like these across your entire attack surface, helping you prioritize what really matters and take precise action before attackers do. Book a scan 🔗 and learn more about how RedHunt Labs can strengthen your exposure management.

