Explore Payment Gateways Through an Attacker’s Lens | Inside the Payment Gateway Integrations Security Handbook
Payment gateways are built to move money reliably. Attackers view them as systems built on trust, timing, and assumptions. A gateway that works consistently is not a sign of safety. It is a stable environment to study, probe, and eventually abuse.
This blog examines payment gateways from an attacker’s perspective, grounded in real exploitation patterns and reinforced with direct insights from industry experts. These patterns are documented extensively in the RedHunt Labs Payment Gateway Integrations Security Handbook 🔗, which maps how attackers turn small logic gaps into large financial impact.
How Attackers Learn Your Payment Flow
Attackers begin with legitimate transactions. They do not rush to exploit. They observe.
They trace how a payment moves from frontend to backend, how callbacks update order state, which signals trigger fulfillment, and where third parties are trusted implicitly. Every successful transaction answers a question.
Our Payment Gateway Integrations Security Handbook 🔗 shows how attackers systematically map:
- Where amounts are finalized
- Which system marks a transaction as paid
- How retries and failures are reconciled
- What happens when events arrive out of sequence

What Attackers Target First
Once the flow is understood, attackers look for leverage points.
Callbacks and webhooks
Poorly authenticated webhooks allow attackers to simulate payment success. If your system trusts the event more than the money movement, the gateway becomes an oracle.
Parameter manipulation
Weak server-side validation allows amounts, currencies, or order references to be altered while preserving a valid flow.
Access control failures
Refunds, retries, and reconciliation endpoints are often exposed to users or services that should never reach them.

Sensitive data exposure
Tokens, API keys, and sometimes even card data surface in logs, error traces, or third-party tools.
Ankur Bhargava, Head of Product Security at PhonePe, captures the layered nature of this risk clearly:
Ankur Bhargava, Head of Product Security at PhonePe
A secure gateway is a stack, not a switch: encrypt in transit, tokenize at the edge, enforce MFA, run real fraud detection, and treat PCI DSS as the floor. Compliance gets you live; security keeps you alive.
Chaining Small Gaps: Retries, Race Conditions, and Refunds
Individual flaws in payment flows may look minor, but attackers are experts at chaining them. Some common abuse patterns include:
- Retry abuse: Payment forms often allow multiple retries for failed transactions. If the system does not correctly reconcile the retries with the actual payment status, attackers can generate “ghost” orders or duplicate credit.
- Race conditions: These occur when two or more processes interact with a shared resource concurrently. In a payment flow, an attacker might simultaneously trigger a transaction and a refund or manipulate order status updates.
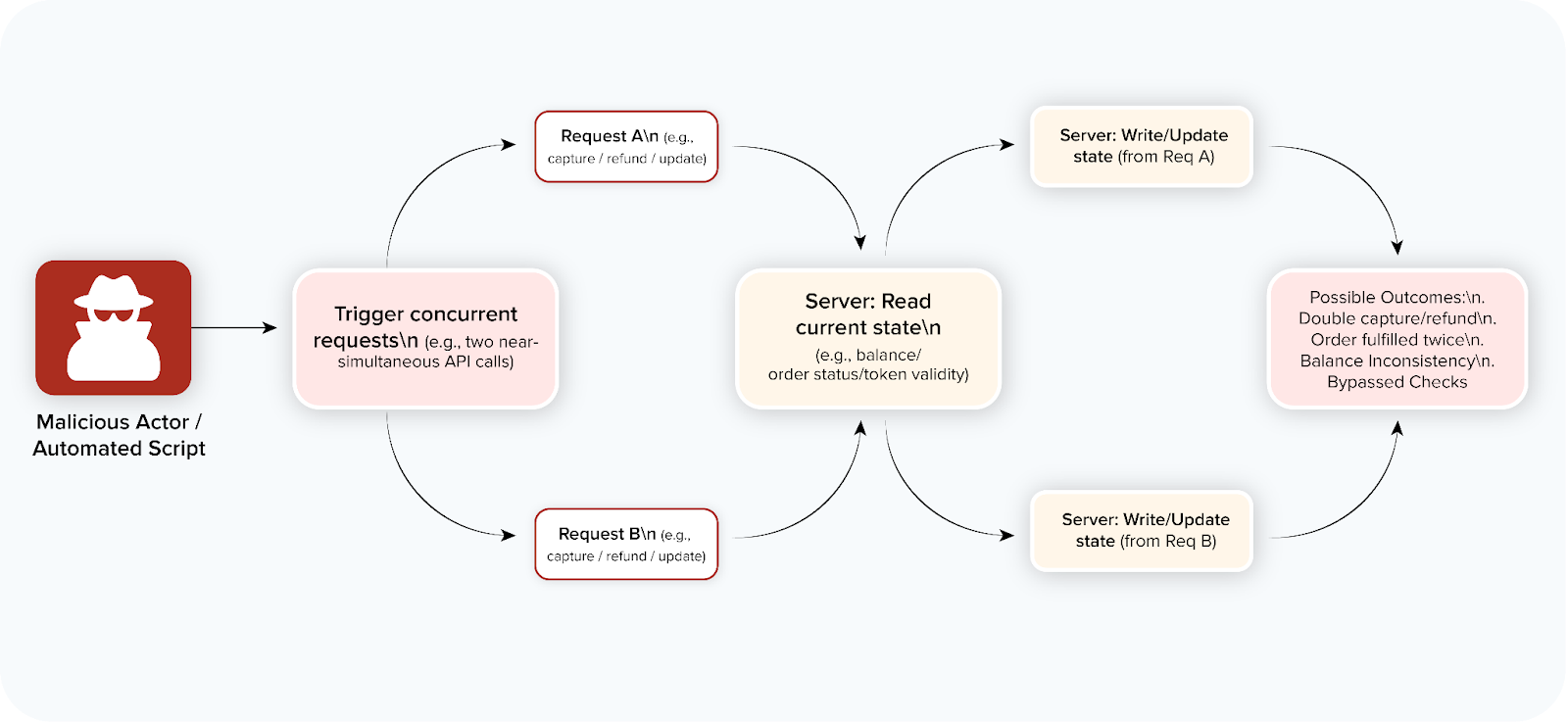
- Refund and chargeback logic gaps: Refund workflows that are not tightly controlled can be exploited to reclaim money or trigger cascading reversals, particularly when paired with weak authentication.
Why Working Payments Still Fail Security
Modern payment gateways rely on plugins, processors, fraud engines, and orchestration platforms. Each dependency extends trust beyond your perimeter.
Anant Shrivastawa, Founder of Cyfinoid Research, warns against implicit trust:
Anant Shrivastawa, Founder at Cyfinoid Research
Every model, prompt, and plugin is a link in the payment supply chain. Assume it is untrusted. Reduce outbound data, limit access, keep record of evidence, and watch the environment in real time so innovation does not trade away confidentiality.
A transaction completing successfully does not prove that the right amount was charged, the correct user was authorized, or even that the event was genuine. This is why vulnerabilities often surface late, during fraud investigations or post-incident reviews.
Ashwath Kumar, Head of Security at Razorpay, emphasizes this risk:
Ashwath Kumar, Head of Security at Razorpay
Money movement has always been a magnet for attacks, and securing it requires more than surface-level checks. It demands a deep understanding of every integration, dependency, and nuance in the payment flow. Most importantly, we must avoid assumptions and instead validate each step end-to-end.
The Leadership View on Trust and Scale
At scale, payment security failures erode trust faster than almost any other issue.
Himanshu Das, CISO at CRED, frames the challenge clearly:
Himanshu Das, CISO at CRED
Security leadership today means finding the balance between risk and user experience. The real goal is to build systems people can trust without slowing innovation.
That balance becomes fragile as payment ecosystems grow more interconnected. Trust is no longer shaped only by user experience, but by how consistently security controls operate across gateways, partners, and backend systems, often without being visible to end users.
From a regulatory and ecosystem perspective, Dr. Sanjay Bahl, Director General at CERT-In, reinforces the foundation:
Dr. Sanjay Bahl, Director General at CERT-In
Today the backbone of an innovative, frictionless secure digital payment gateway inclusive of encryption, authentication, audits, and compliance is fundamental for inspiring trust amongst merchants and customers while ensuring that both are protected in every transaction through adaptive, intelligent, and invisible cyber defenses.
What This Means for Teams
If you own payment flows, this means:
- Success responses are not proof of security
- Callbacks and webhooks must be treated as hostile input
- Trust boundaries must be tested, not assumed
These are design problems, not edge cases.
Why This Handbook Is Not Optional Reading
Most payment documentation shows teams how to make integrations work. But only very few shows how those same integrations are exploited in the real world.
The RedHunt Labs Payment Gateway Integrations Security Handbook 🔗 exists to close that gap. It connects attacker behavior, expert insight, and real pentest findings into a single, practical reference.
Compressed to its essence, the handbook helps teams:
- Think like attackers before attackers do
- Identify logic flaws QA and audits miss
- Validate trust across third-party dependencies
- Stress-test payment flows end-to-end
It is used across roles, from security and engineering to payments and risk, because attacker behavior does not respect org charts.
Final Thoughts
Attackers do not break payment gateways. They follow the rules more precisely than the systems expect. Industry experts agree that layered defenses, constant validation, and skepticism of trust are essential in modern payment systems. Those same themes repeat across real-world breaches.
If your gateway works but has never been examined through an attacker’s lens, you are only seeing half the system. The RedHunt Labs Payment Gateway Integrations Security Handbook documents the other half. Because the most dangerous payment flows are the ones that work perfectly.
.
See how attackers actually break payment flows, documented from real scenarios.
Learn More from our Payment Gateway Integrations Security Handbook.
.


