PCI DSS v4.0.1 for Payment Integrations: A Realistic Security-First Approach
Modern payment integrations are fast, flexible, and increasingly complex. APIs talk to gateways, webhooks trigger state changes, third parties handle fraud, retries, refunds, and orchestration layers quietly sit in between. In most teams, the signal that things are “working” is simple: transactions go through. That signal is misleading.
At RedHunt Labs, we found that the real-world payment pentests reveal the common mistake of treating PCI DSS as a finish line instead of a baseline. This blog reframes what PCI DSS is meant to do, highlights where modern payment integrations quietly fail, and shows how the Payment Gateway Integrations Security Handbook helps teams move beyond checkbox compliance toward real security resilience.
TL;DR for Busy Payment Teams
- PCI DSS is a security baseline
- Working transactions are not a security signal
- Most payment integration vulnerabilities live in logic, not crypto
- Webhooks, retries, and refunds are the most abused components
- Audits confirm control presence; attackers test control behavior
- The Payment Gateway Integrations Security Handbook 🔗 covers these gaps with real test cases
Why PCI DSS Must Be Treated as a Security Standard
PCI DSS v4.0.1 focuses heavily on intent: protecting cardholder data, ensuring transaction integrity, and reducing abuse opportunities. None of that is achieved by simply passing an audit.
When PCI DSS is treated as a compliance checkbox, teams optimize for evidence. When treated as a security standard, teams optimize for abuse resistance. This distinction matters.
Meeting PCI DSS security objectives means validating that controls hold up under misuse, not just that they exist on paper.
Why “It Works” Is Not a Security Signal
Functional success is the weakest indicator of payment security. QA validates happy paths. Attackers look for valid abuse paths.
In real payment integrations, vulnerabilities often live in places QA never touches:
- Backend APIs that trust frontend validation
- Webhooks that assume gateway authenticity without verification
- Retry logic that creates inconsistent state
- Refund flows that bypass access controls
- Tokens logged, reused, or scoped too broadly
A checkout can succeed every time and still allow an attacker to manipulate amounts, replay transactions, or unlock value without paying.
From a PCI DSS security perspective, this matters because the standard assumes adversarial behavior. If controls only work when everything behaves nicely, they are not controls.
Our Payment Gateway Integrations Security Handbook 🔗 explicitly addresses this gap. It documents scenarios where legitimate flows were exploited without breaking anything, precisely the kind of failures that compliance-only reviews miss.
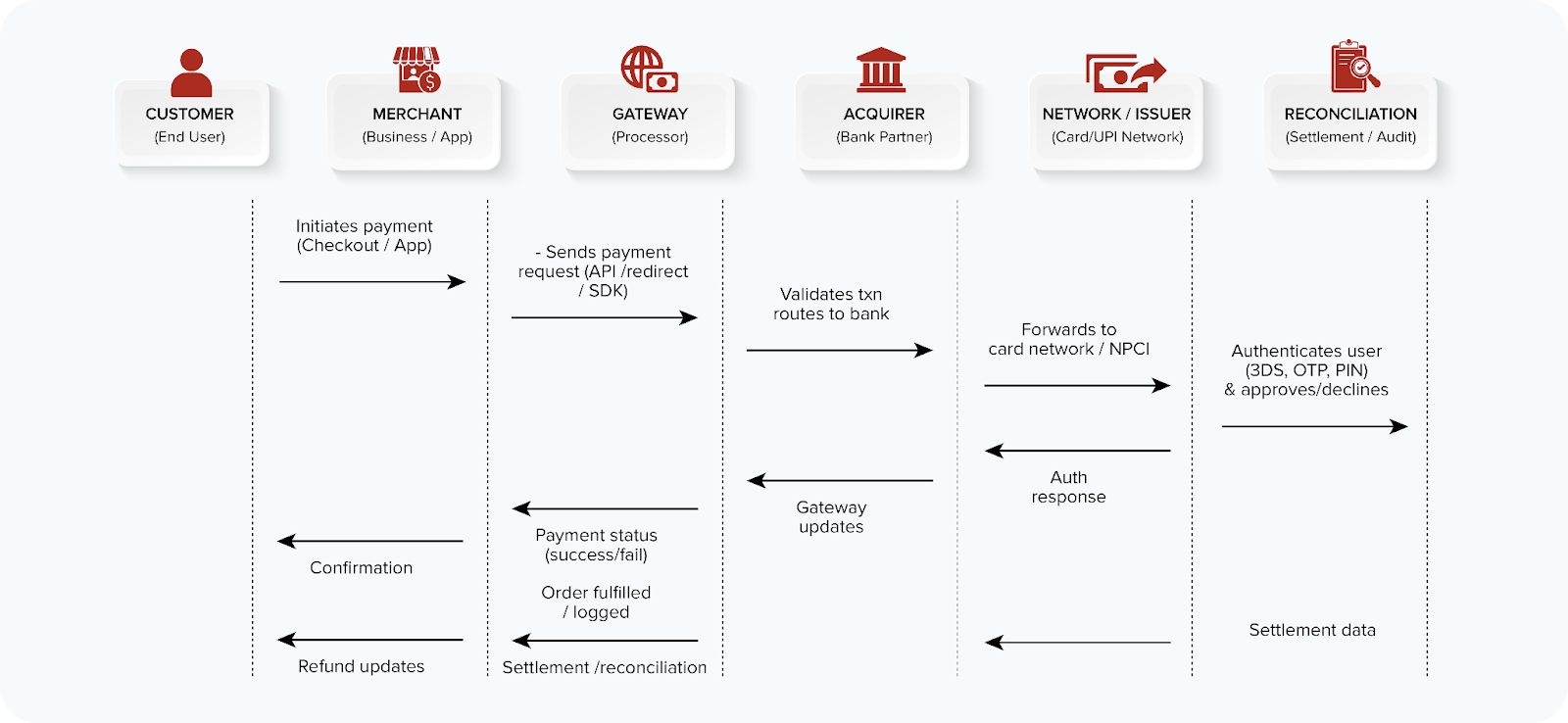
How Modern Payment Models Quietly Expand Risk
Payment architecture determines where PCI risk lives.
- Direct API Integrations
If your backend touches tokens or card data, even briefly, it is in scope. Logs, retries, memory, and error handling all become part of the attack surface, whether you intended storage or not. - Redirect and Hosted Pages
Redirects reduce exposure, not responsibility. Callbacks, return URLs, session binding, and token exchanges still need protection. A weak callback alone can mark an order as paid without funds moving. - Webhooks and Asynchronous Flows
Webhooks are among the most abused payment components. They bypass user interaction, are often weakly authenticated, and poorly monitored. PCI DSS expects integrity and authenticity here, not blind trust in the gateway. - Third-Party Platforms and Orchestration
Plugins, fraud tools, and aggregators quietly expand risk. PCI responsibility does not transfer to vendors, and misconfigurations or excessive permissions routinely widen scope without visibility.
Common PCI Misunderstandings That Create Real Risk
Security teams often encounter the same misconceptions during audits and assessments:
- “We do not store card data, so we are out of scope.”
Transmission, logging, token handling, and retries still count. - “Tokens are safe by default.”
Poorly scoped or reused tokens are treated as sensitive data by attackers and auditors alike. - “The gateway handles security.”
Gateways secure their side. Your integration logic is still yours. - “The audit passed last year.”
Payment flows change faster than audit cycles.
These misunderstandings explain why vulnerabilities surface late, often during incidents or fraud investigations rather than during planned security reviews.
Why Audits Alone Miss Payment Logic Failures
PCI audits verify the presence of controls, but sometimes Pentests tell a different story.
Real-world payment pentesting consistently uncovers issues that may look compliant on paper but fail under adversarial testing:
- Order marked paid before gateway confirmation
- Refund endpoints callable without proper authorization
- Race conditions between payment success and cancellation
- Replayable callbacks
- Price validation only on the frontend

These might not break PCI requirements directly, but the spirit of PCI as a security standard.
Why This Is the One Resource Payment Teams Should Not Skip
Security documentation usually falls into two buckets: vendor docs that explain how to integrate, and compliance docs that explain how to pass audits. At times, both of these skip explaining how integrations fail in the real world. The Payment Gateway Integrations Security Handbook 🔗 exists for that missing space.
It is useful because it is practical:
- Written for security engineers, developers, payment ops, and product teams
- Based on real pentest findings, not theory
- Focused on logic flaws, retries, race conditions, refunds, and third-party risk
- Vendor-neutral and applicable across gateways
Instead of treating security as a phase, it embeds it across the payment lifecycle. Here’s how it actually helps along each phase:
- Before integration, to understand architectural risk
- During development, to avoid known logic traps
- Before launch, to test abuse paths
- After launch, to find silent failures early
Final Takeaway
A payment system that works is not necessarily secure and resilient.
Security teams that treat PCI DSS as a living security standard, test beyond happy paths, and challenge assumptions consistently outperform those that treat it as annual compliance work.
Because in payments, the real question is not whether it works, but whether it holds up when someone tries to break it.
.
If your team handles payments, this is not optional reading.
Learn Best Practices from our Payment Gateway Integrations Security Handbook
.


