RedHunt Labs ASM Portal 2024 Wrapped: A Year of Transformative and Game-changing Enhancements
The Journey So Far
As organizations navigate the complexities of modern attack surfaces, staying ahead of evolving threats requires constant innovation. At RedHunt Labs, 2024 has been a year of significant advancements in our Attack Surface Management (ASM) platform. From improving operational efficiency to introducing features that simplify risk management, our focus has been on making your security workflows smarter, faster, and more effective.
In this post, we’ll walk you through the key updates and enhancements rolled out this year. These additions are not just upgrades—they are solutions crafted to tackle real-world challenges, streamline processes, and provide actionable insights that empower your security team.
Table of Contents
- The Journey So Far
- Product Management Features Launched
- 1. ASM Scoring for Organizational Insights
- 2. Supply Chain and Third-Party Risk Management
- 3. Advanced Third-Party Asset Discovery
- 4. RedHunt ASM Platform – Now available in AWS Marketplace
- 5. CSPM: Extending ASM for Unified Cloud Security
- 6. Visualize Your Exposures with the Attack Surface Graph
- 7. Asset Prioritization Groups
- 8. Proactive Data Leak Prevention
- 9. Prioritize What Matters with Asset Scoring
- 10. Stay Informed with Third-Party Asset Notifications
- 11. Streamlined Bug Tracking with ServiceNow Integration
- 12. Weekly Summary Reports
- 13. Partner Portal for On-Demand Scans
- 14. Whitelisted IP Transparency
- Intrinsic Features Added
- Under-The-Hood Improvements
- Wrapping It Up
Product Management Features Launched
1. ASM Scoring for Organizational Insights
Our ASM Scoring isn’t just another vanity metric—it’s designed to provide a meaningful, actionable measure of your organization’s security posture. Unlike cosmetic scores seen on many platforms, our system leverages real data points from your external attack surface to offer insights that matter. By analysing risk factors, exposure trends, and remediation progress, the score tracks how your security evolves over time. This allows you to highlight tangible improvements to stakeholders, identify critical areas needing attention, and make informed decisions backed by data. ASM Scoring transforms your security posture into a clear, measurable benchmark, empowering your team to stay ahead of evolving threats.
2. Supply Chain and Third-Party Risk Management
Managing risks across your supply chain is now more secure and collaborative. With our new feature, you can onboard your vendors and subsidiaries into the ASM Portal under a restricted view, ensuring they only access data relevant to their scope. This enables you to share actionable insights with external entities without compromising sensitive information. By empowering your partners to manage their risks within a controlled environment, you achieve complete visibility into your supply chain while maintaining strict data boundaries.
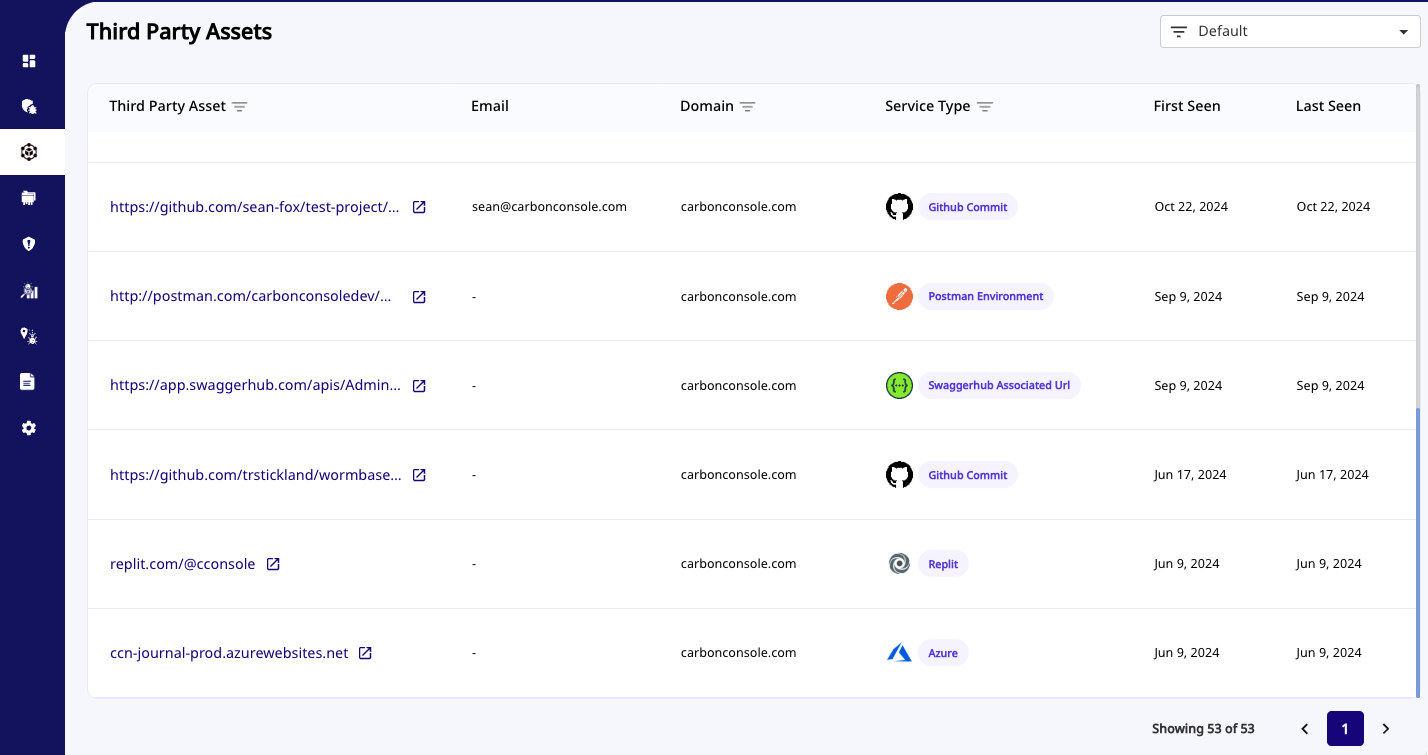
3. Advanced Third-Party Asset Discovery
This year, we enhanced our Third-Party Asset Discovery feature to include additional services such as Postman collections, BlueJeans, Azure CloudApp, Azure Websites, and more. These resources, if left unsecured, can expose sensitive information like API keys, configurations, or internal data. By actively identifying and analyzing such assets across the internet, including those not managed directly by internal teams, we provide real-time visibility and risk analysis. This ensures organizations can proactively address exposures, reducing the risk of third-party vulnerabilities affecting their security posture.
4. RedHunt ASM Platform – Now available in AWS Marketplace
Last year, we partnered with AWS Marketplace to make it easier for organizations to procure the RedHunt Labs ASM Portal. This partnership enables businesses to seamlessly purchase our services while leveraging AWS credits for efficient budget management. By integrating with AWS’s enterprise-friendly workflows, we’ve streamlined the procurement process, ensuring a faster and more convenient way to adopt our platform and strengthen your security capabilities.

5. CSPM: Extending ASM for Unified Cloud Security
This year, we introduced Cloud Security Posture Management (CSPM) as an optional add-on to seamlessly integrate with our ASM platform. This addition aligns with our vision of providing a single platform for users to manage their entire attack surface, both external and cloud-specific. While the ASM platform focuses on external risks, CSPM complements it by addressing internal cloud infrastructure risks such as misconfigurations, compliance gaps, and cloud-native vulnerabilities. By combining these capabilities, users benefit from a unified solution that provides comprehensive visibility and control over their security posture, reducing complexity and streamlining workflow.
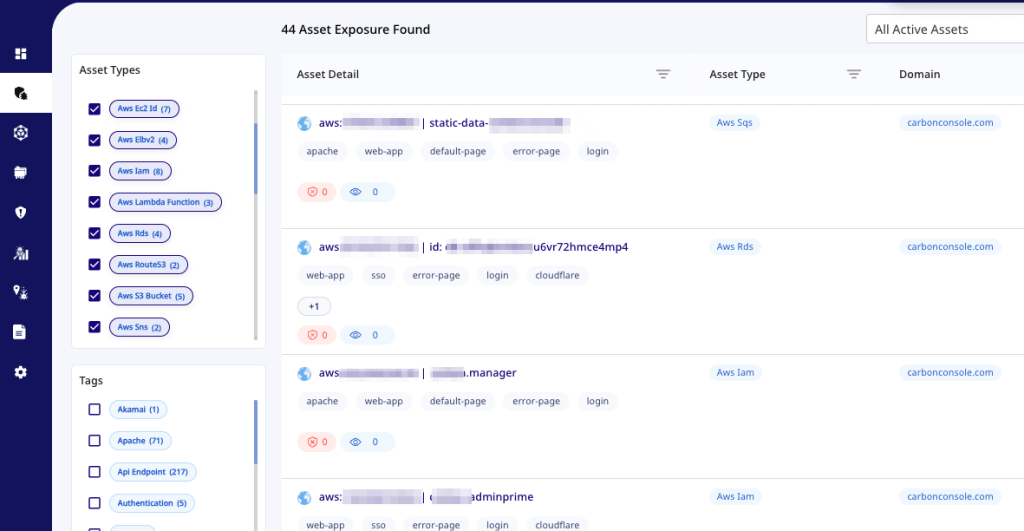
6. Visualize Your Exposures with the Attack Surface Graph
Visualizing your attack surface helps you identify and address vulnerabilities more effectively. Our new Attack Surface Graph provides an intuitive visualization of your organization’s exposure. Using advanced filters, you can pinpoint attack paths and navigate complex relationships between assets with ease.
7. Asset Prioritization Groups
In environments where multiple web applications redirect to a single app or share similar functionalities, it can be challenging to distinguish critical targets from redundant assets. Our Asset Prioritization Groups tackle this issue by intelligently categorizing assets based on their relevance, uniqueness, and risk profile. This ensures that high-value applications, such as primary web apps (groups) or production systems, are highlighted while redundant or redirecting applications are deprioritized.
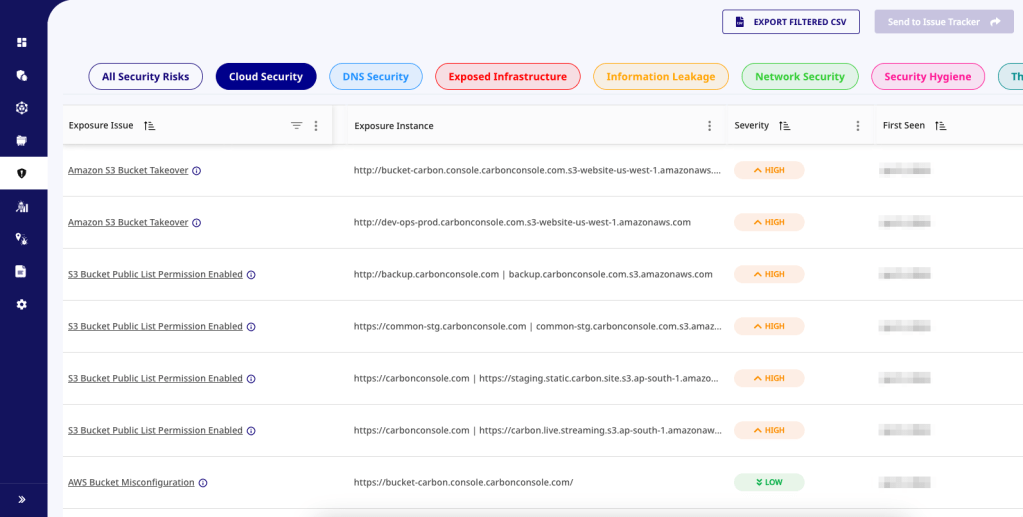
8. Proactive Data Leak Prevention
Our new feature tracks commits made using corporate emails on platforms like GitHub and GitLab. This helps identify and monitor not just leaked credentials but also sensitive files, internal source code, urls, or configurations that could lead to data exposure.
9. Prioritize What Matters with Asset Scoring
Understanding the importance of each asset in your attack surface is critical for efficient security workflows. Our Asset Importance Scoring uses a comprehensive set of parameters—such as cookies, DOM length, HTTP headers, SSL certificates, status codes, favicon analysis, and more—to evaluate each asset’s relevance. This feature is particularly useful in identifying DAST / Pentest Candidates, ensuring that security teams focus on high-value targets rather than wasting time on low-priority or irrelevant assets.
10. Stay Informed with Third-Party Asset Notifications
Staying updated on new discoveries is crucial for managing risks effectively. With our notification system, you’ll receive alerts whenever third-party assets are discovered. Notifications are configurable, so you can focus on updates that matter most to your organization.
11. Streamlined Bug Tracking with ServiceNow Integration
To better support large enterprises, we introduced ServiceNow integration to enhance workflows for bug tracking and incident management. This integration allows organizations to centralize their reporting, remediation, and resolution processes within ServiceNow’s robust platform.
12. Weekly Summary Reports
For organizations that prefer periodic updates, our platform now offer Weekly Summaries. These reports provide insights into new assets discovered, risks identified, leaks exposed, and remediation efforts completed in the past week. This feature keeps teams informed and ensures ongoing progress tracking.
13. Partner Portal for On-Demand Scans
Designed for Managed Security Service Providers (MSSPs) and Bug Bounty Hunters, the Partner Portal allows you to launch on-demand scans for your customers. This feature supports flexible workflows, enabling MSSPs to cater to diverse client needs. Currently, access is available via a waitlist as we continue to refine this offering.
14. Whitelisted IP Transparency
One of the biggest challenges during an incident handling is differentiating between legitimate and malicious traffic. To address this, we’ve introduced a feature that lists all our IP addresses used by RedHunt Labs scan engines. With this transparency, you can quickly identify legitimate traffic during investigations, saving time and improving accuracy when responding to incidents.
Intrinsic Features Added
Along with these management features, we also worked a lot on technical features many of which are listed below:
1. Comprehensive Cloud Asset Inventory
This year, we extended our cloud integration capabilities to include AWS, GCP, Azure, and DigitalOcean, giving you complete visibility into your cloud environments. This ensures that all assets—ranging from storage buckets to compute instances—are accounted for and monitored.
2. Historical URL Enumeration and Scanning
Sensitive information can often remain exposed in legacy systems. To combat this, we introduced tools to analyze historical URLs, helping you uncover potential data leaks from outdated systems or previously misconfigured environments.
3. CVE Tracking and Scanning
By integrating real-time CVE tracking with EPSS scores, we ensure vulnerabilities are automatically mapped to discovered assets. This allows faster prioritization and remediation of critical issues, keeping your organization secure from emerging threats.
4. Advanced Web Application Secret Scanning
We added our web crawling tools to extract secrets from JavaScript files and HTTP responses. This ensures sensitive information inadvertently exposed by web applications is identified quickly, helping you secure critical data.
5. Intelligent URL Detection
Our platform now supports tech-specific URL enumeration, tailoring discovery to match the underlying technology stack. This allows us to uncover hidden entry points, which might otherwise be missed, enhancing your organization’s ability to defend against exploitation.
6. Default Credential Detection
Default credentials are often overlooked but represent significant security risks. To address this, we automated the detection of default credentials across all discovered assets, ensuring weak authentication mechanisms are flagged and addressed proactively.
Under-The-Hood Improvements
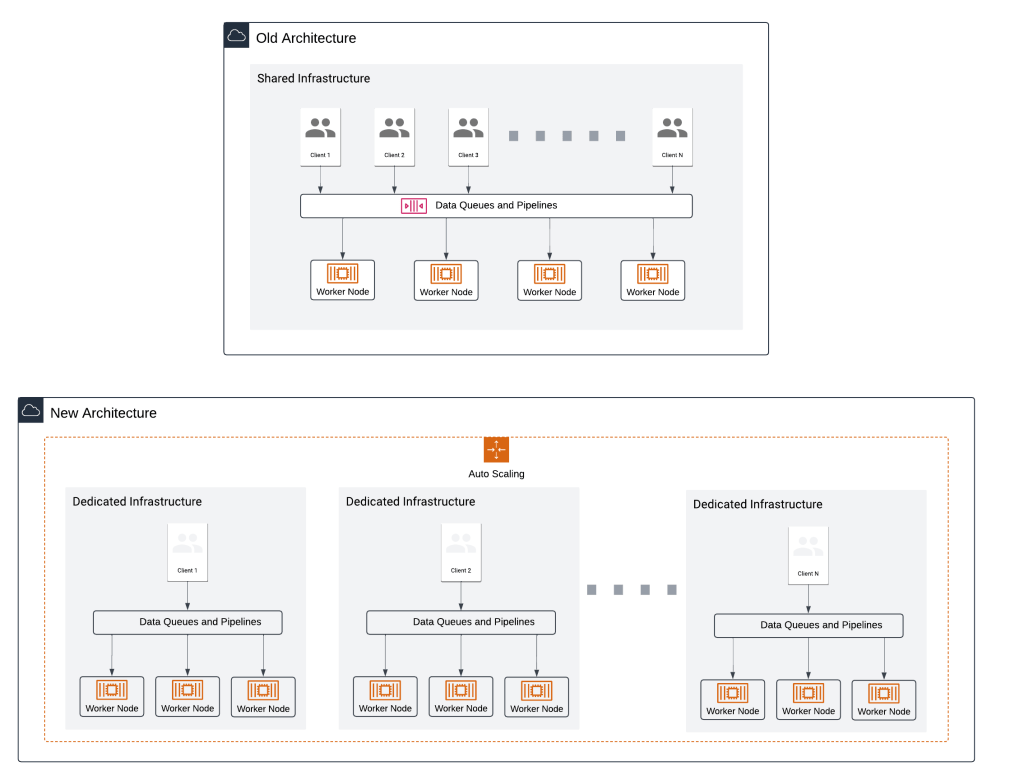
1. Separate Clusters for Heavy and Light Tools
Previously, all tools operated within shared queues, leading to delays and inefficiencies. We now use separate clusters for heavy and light tools, enabling:
- Infinite scalability.
- Cost optimization with no wasted resources.
- Faster scans due to dedicated queues.
2. Improved Scalability with Queue Management
Scalability is key to handling growing workloads, and our new queue management system delivers just that. With truly auto-scaling infrastructure, resources are dynamically provisioned based on demand, eliminating the need for pre-allocated fixed resources. This ensures seamless scaling while optimizing costs by allocating resources only when required. The result is a system that can handle spikes in workload effortlessly, providing unmatched efficiency and reliability for our users.
3. Optimized Elastic Log Shipping
To enhance log shipping reliability and performance, we transitioned from local loggers to AWS SQS plugins. This shift eliminated dependencies on on-prem infrastructure, improving scalability and reducing the risk of hardware-related bottlenecks. The new system ensures logs are securely and efficiently shipped, enabling smoother operations and supporting the needs of modern cloud-native architectures.
4. Research-Side Enhancements for Data Discovery
To process the ever-increasing volume of data, we transitioned our research engine to a serverless architecture. This change enabled us to handle over 20TB of data monthly, eliminating issues tied to local hardware like disk or memory limitations. By leveraging serverless infrastructure, we not only improved reliability but also reduced costs, ensuring consistent and scalable performance to meet the demands of our data-intensive operations.
5. Data Collection: 9x Scale-Up
Our optimized research engine has significantly boosted data collection capabilities, with subdomain discovery increasing from 4 million to 20 million daily. In some instances, performance improvements reached an impressive 9x scale-up, allowing us to process and analyze data at unprecedented speeds. These enhancements ensure more comprehensive coverage, providing users with deeper insights into their attack surface.
6. Frontend Migration to CDN
To improve user experience, we migrated our front end to Content Delivery Network (CDN) endpoints, resulting in improved stability, increased availability, and faster response times. Users now experience 20x faster performance, ensuring a seamless and responsive interface even during peak usage. Additionally, this migration has optimized costs by offloading traffic to distributed CDN nodes, providing better scalability and resilience.
Wrapping It Up
2024 has been a transformative year for our platform, reflecting our commitment to supporting organizations in strengthening their security posture. With these enhancements, we aim to make attack surface management not only comprehensive but also intuitive and efficient.
As we look ahead, our focus remains on innovation, collaboration, and delivering features that address the needs of a dynamic cybersecurity landscape. We’re excited about what’s to come and invite you to explore these features to see how they can make a difference in your security operations.
.
Curious about how these updates can work for you?
See them in action today!
.