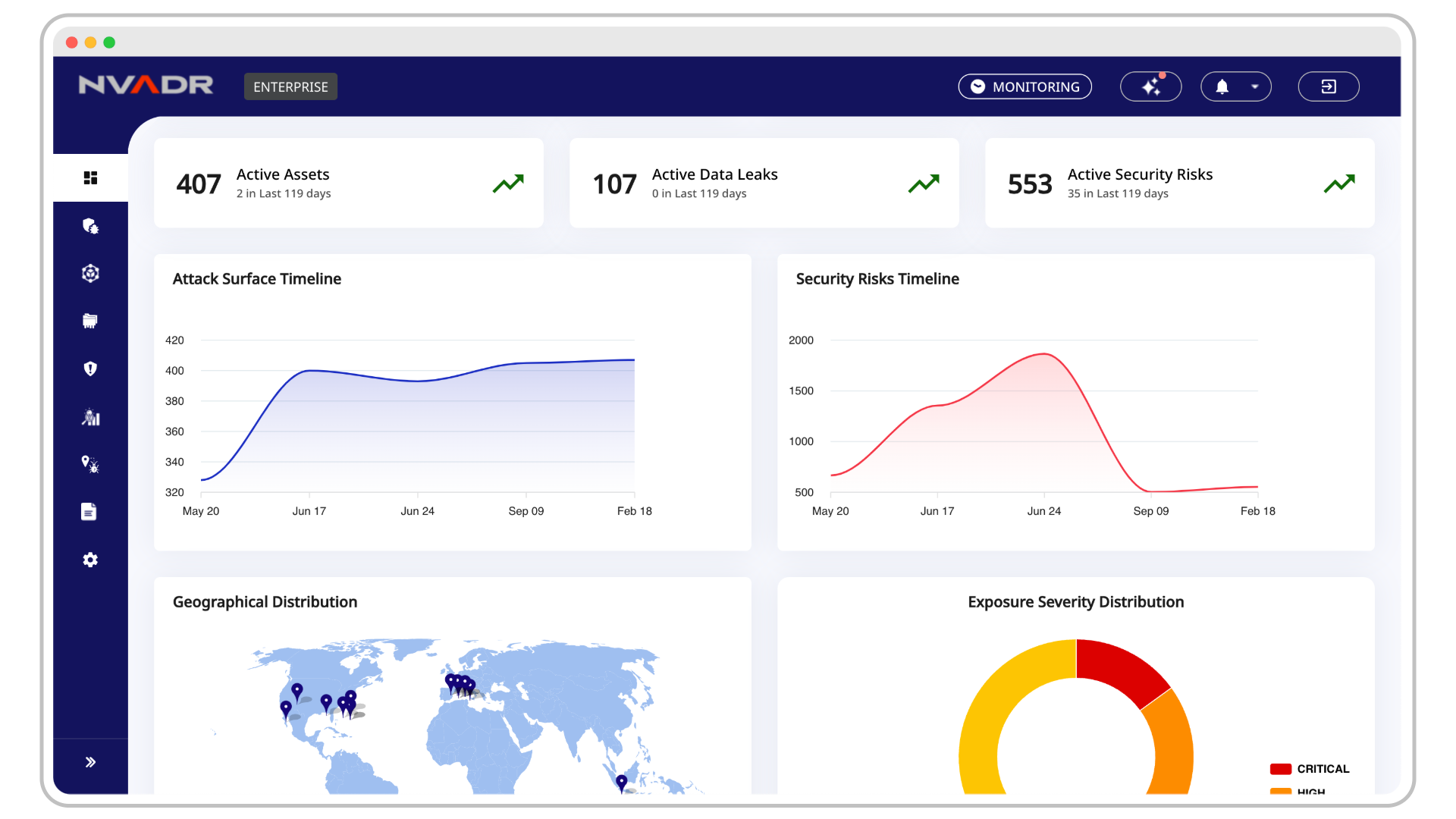
The Top 7 Emerging Threats That ASM Can Help Detect Before It’s Too Late
The cybersecurity landscape never stays the same for long. New threats emerge, old ones evolve, and attackers find fresh ways to exploit vulnerabilities. As businesses expand their digital footprint, they unknowingly widen their attack surface, making it even harder to keep track of potential risks.
This is where Attack Surface Management (ASM) comes into play. By continuously monitoring and analyzing your digital presence, ASM helps you spot threats early before they spiral into full-blown security incidents.
At RedHunt Labs, we specialize in Attack Surface Management, helping businesses proactively discover, monitor, and secure their digital assets. Our platform provides deep visibility into your attack surface, ensuring that emerging threats are identified before they become critical risks.
Let’s break down seven emerging threats that ASM can help detect before they cause chaos:
1. Shadow IT & Untracked Assets: The Accidental Backdoor
What is it?
Employees often deploy cloud applications, set up third-party tools, or even spin up entire servers without IT approval. While this makes their work easier, it also introduces unmonitored and unsecured assets into the company’s attack surface. These shadow IT resources often lack the security controls that official IT-managed systems have, making prime targets for attackers looking for an easy way in.
Why ASM Helps:
Organizations need full visibility into their digital footprint to track and secure unauthorized assets. Attackers constantly look for overlooked entry points, and without ASM, these unknown systems can remain exposed for months.
How RedHunt Labs Helps:
Our Discovery Engine continuously scans the internet for unknown assets connected to your organization. Whether it’s an abandoned subdomain or an unsanctioned cloud storage bucket, RedHunt Labs ASM helps security teams take back control.
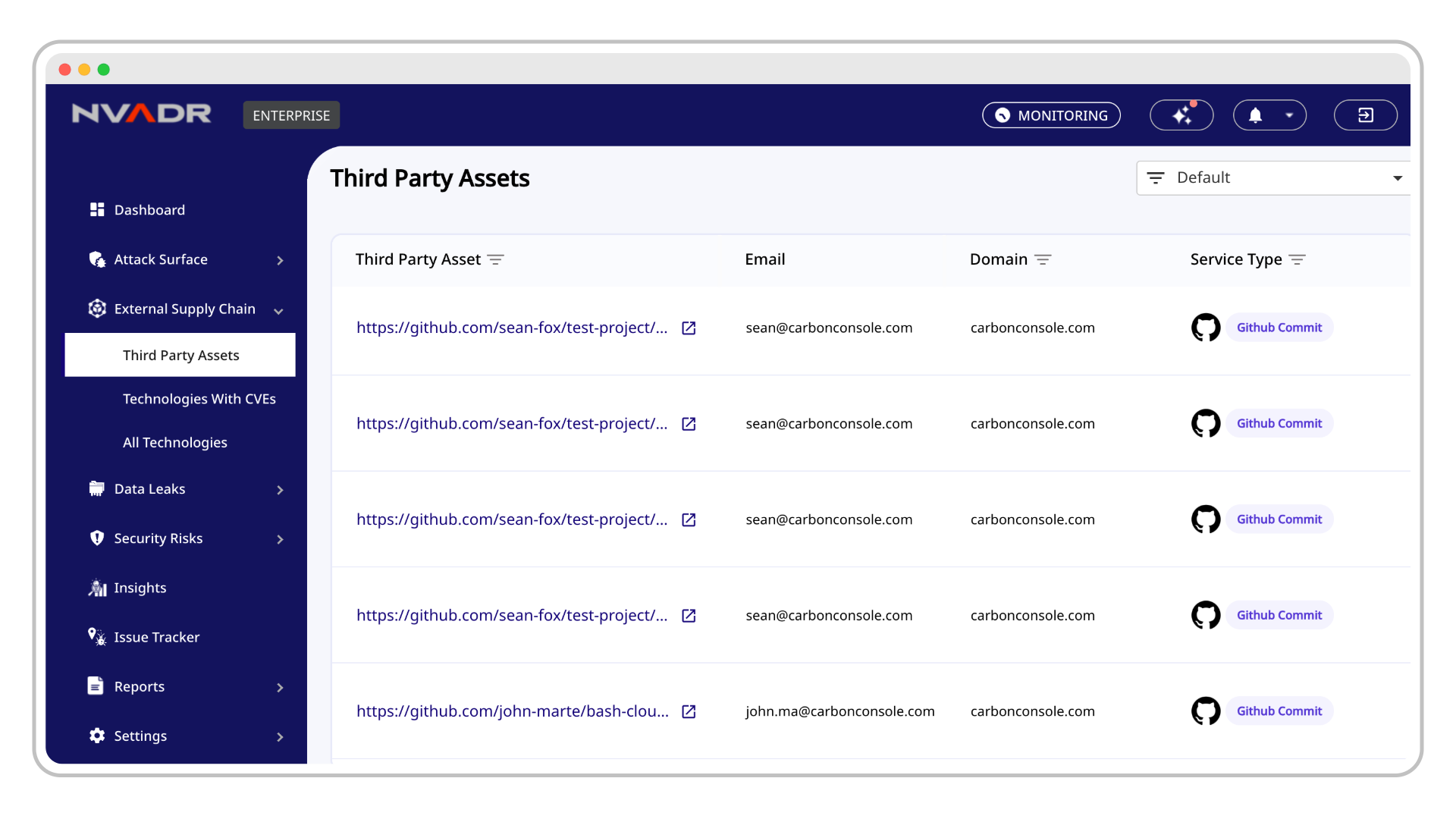
2. Third-Party SaaS Exposures: Your Security is Only as Strong as Your Weakest Link
What is it?
Many organizations depend on a variety of SaaS applications and cloud-based tools to streamline their operations. However, these services can introduce hidden risks—vulnerabilities in the software, misconfigurations, or lapses in security protocols can leave your sensitive data exposed. A breach in one of these SaaS platforms can have a domino effect, impacting not just the vendor but your entire ecosystem.
Why ASM Helps:
Organizations need a continuous, in-depth view of all their SaaS integrations to identify potential security gaps and misconfigurations early on. ASM provides that external perspective, allowing you to see and secure every point of interaction with third-party software.
How RedHunt Labs Helps:
RedHunt Labs’ Third-Party Risk Monitoring feature goes beyond standard vendor evaluations—it continuously scans and assesses your SaaS applications for vulnerabilities and exposures. By doing so, our ASM platform alerts you immediately when a risk is detected, enabling you to take proactive steps to secure your data before a potential breach occurs.
3. Forgotten Subdomains: The Digital Ghost Towns
What is it?
Over time, companies create subdomains for campaigns, testing, or temporary projects. These often remain active long after they’ve been abandoned, creating security gaps. Attackers can hijack these forgotten subdomains through subdomain takeovers, where they register expired DNS records and use them for phishing, malware distribution, or data exfiltration.
Why ASM Helps:
Security teams need continuous visibility into their DNS infrastructure to ensure no forgotten subdomains remain vulnerable. Without monitoring, subdomain takeovers can go unnoticed until it’s too late.
How RedHunt Labs Helps:
Our Continuous Subdomain Monitoring discovers and keeps track of all your subdomains, ensuring none of them are hijacked or left exposed.

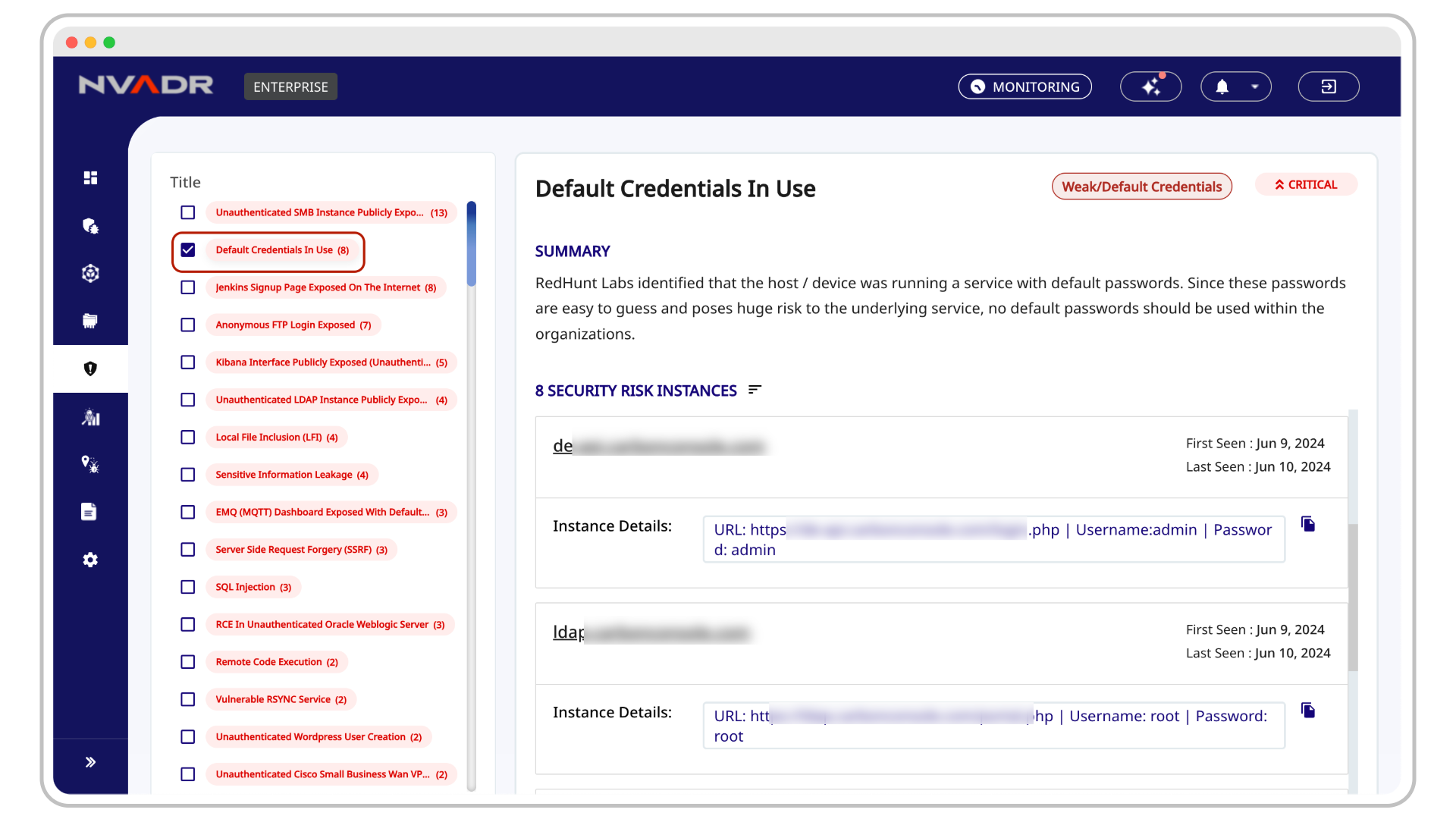
4. Exposed Credentials: The Keys to Your Kingdom
What is it?
Data breaches often leak usernames and passwords, which are then sold on dark web marketplaces. Attackers use these stolen credentials for credential stuffing attacks, where they try breached usernames and passwords across multiple platforms, hoping to gain unauthorized access.
Why ASM Helps:
Detecting compromised credentials early can prevent account takeovers, financial fraud, and corporate espionage. Organizations need to monitor for leaked credentials and enforce strong password policies.
How RedHunt Labs Helps:
Our Credential Exposure Detection scans breach data and alerts you if employee credentials are exposed, allowing you to take action before attackers can exploit them.
5. Misconfigured and Vulnerable Web Applications: The Open Doors to Data Theft
What is it?
Organizations often deploy web applications that, if not properly configured or updated, can expose critical vulnerabilities. Misconfigured APIs, insecure default settings, or outdated frameworks can open doors for attackers, leading to unauthorized access or data breaches.
Why ASM Helps:
Maintaining secure web applications requires continuous oversight to catch misconfigurations and vulnerabilities as soon as they appear. ASM offers an external perspective that pinpoints these weaknesses before they can be exploited.
How RedHunt Labs Helps:
RedHunt Labs’ Security Vulnerability Scanning modules extend its monitoring to include your web applications, identifying misconfigurations and outdated components. This proactive approach enables your security teams to address vulnerabilities promptly and reduce the risk of exploitation.

6. Outdated and Vulnerable Software: The Easy Entry Point
What is it?
Unpatched software and outdated applications are common attack vectors for cybercriminals. Exploiting known vulnerabilities in old versions of web frameworks, plugins, or third-party services can provide attackers with an easy way into your environment.
Why ASM Helps:
Organizations need constant awareness of which software versions they are running and whether they contain known vulnerabilities.
How RedHunt Labs Helps:
Our Technology Fingerprinting feature detects outdated software and highlights potential vulnerabilities, allowing security teams to take preventive action.

7. Rogue GitHub Commits: Accidental Leaks in Code
What is it?
Developers sometimes inadvertently commit sensitive information—such as API keys, credentials, or configuration files—to public repositories. These rogue commits can expose internal secrets to attackers, offering a direct route into your systems.
Why ASM Helps:
Continuous monitoring of public code repositories is essential to catch and remediate accidental exposures before they lead to breaches. ASM helps by scanning for sensitive data leaks within your codebase and alerting you as soon as a risky commit is detected.
How RedHunt Labs Helps:
Our Data Leak Monitoring module detects rogue GitHub commits. By identifying these accidental leaks early and continuously, our platform ensures that sensitive information is quickly secured, safeguarding your organization from potential exploitation.

Final Thoughts
The attack surface of organizations is growing faster than ever. With cloud adoption, third-party integrations, and remote work environments, businesses have more exposed assets than they realize. Threat actors are quick to exploit these blind spots, making continuous monitoring and proactive risk detection non-negotiable.
This is where Attack Surface Management (ASM) becomes crucial. Unlike traditional security approaches that focus on internal defenses, ASM provides an external view of your organization—just like an attacker would see it. By continuously discovering, mapping, and monitoring digital assets, ASM helps security teams gain visibility into unknown risks, detect emerging threats, and take action before attackers do.
Stay Ahead of Threats with RedHunt Labs’ ASM Platform
At RedHunt Labs, we take a holistic approach to Attack Surface Management, combining asset discovery, risk intelligence, and real-time monitoring to give businesses complete control over their external security posture. With the ability to detect shadow IT, third-party risks, misconfigurations, exposed credentials, and more, our platform ensures that security teams are always a step ahead of attackers.
.
Gain full visibility into your attack surface and stay ahead of emerging threats with our ASM platform.
See it in action today!
.

