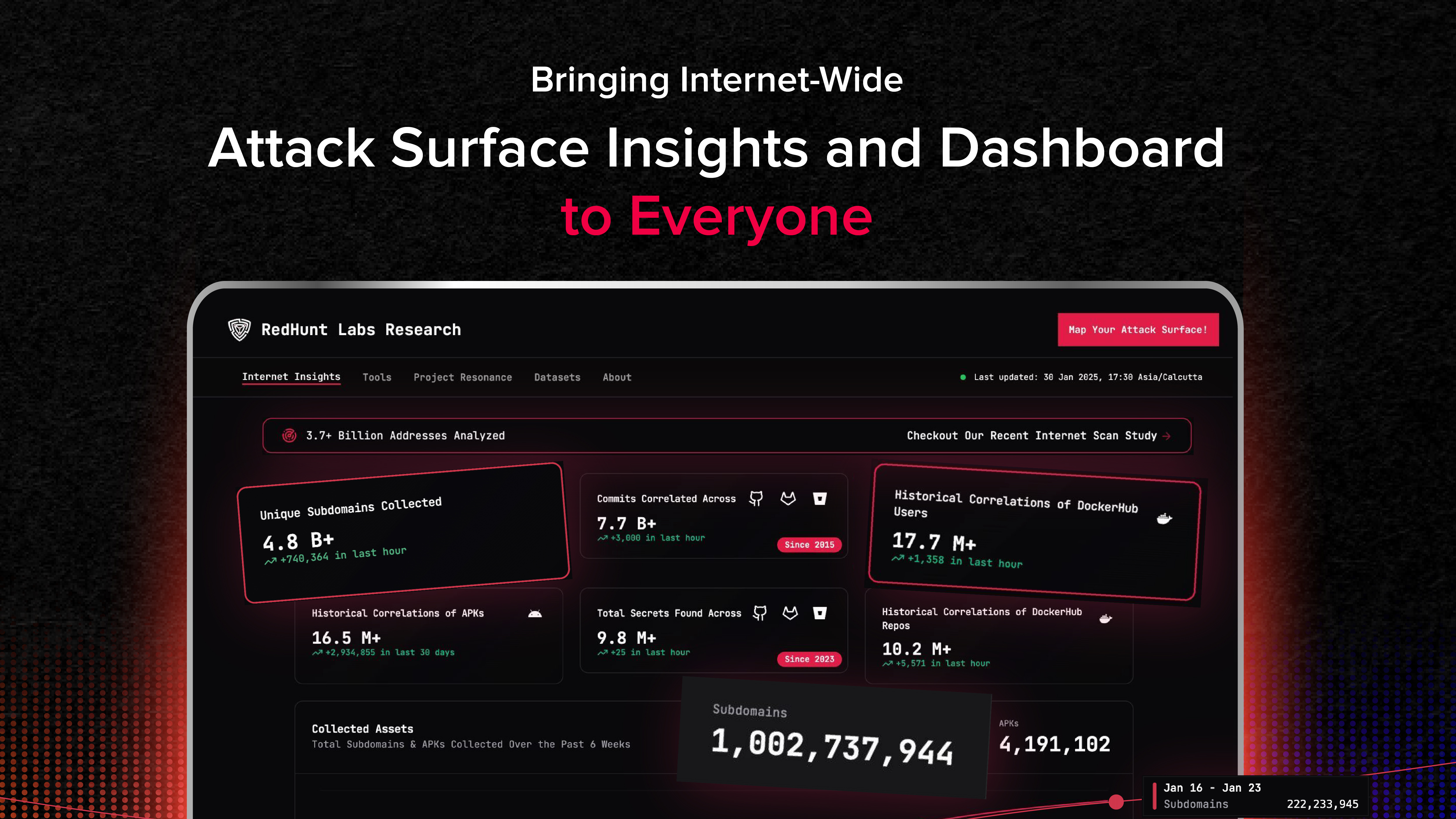
The internet is constantly evolving, and so are the risks that come with it. Organizations, researchers, and security professionals often struggle to keep up with the growing attack surface. But…
Category: Technology
Introduction If you are in the Information Technology sector, you most likely have come across the terms Cloud Object Storage, S3 buckets, and/or buckets. Cloud object storage buckets are like…
Subdomain enumeration holds a critical role in our reconnaissance and Attack Surface Management (ASM) workflows. In this blog, we’ll dive deep into the complexities of subdomain enumeration, exploring the diverse array of tools and techniques available. Furthermore, addressing the challenge of mitigating false negatives, i.e. missing out on subdomains, is paramount for ensuring robust security evaluations.
Introduction In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount. As the digital realm expands, so does the attack surface of organizations, presenting a challenge for…
Intro Typosquatting and phishing are quite a headache for businesses. Creating fake websites that look almost identical to legitimate ones has become a piece of cake for attackers. Experts can…
RedHunt Labs introduces BucketLoot – a cutting-edge, automated S3-compatible Cloud Object Storage bucket inspector designed to empower users in securing their data. BucketLoot offers an array of powerful features, allowing users to seamlessly extract valuable assets, detect secret exposures, and search for custom keywords and Regular Expressions within publicly-exposed storage buckets.
With technological advancements come new security risks that threaten the confidentiality, integrity, and availability of sensitive information. In this blog post, we will explore why managing your external attack surface is essential to securing your organization.
By default, every image pushed to the Docker Hub through your free account appears in the public registry by default. This business strategy of Docker Inc. to engage more people into purchasing their paid subscriptions puts the free users at risk. Once an attacker finds exposed docker images related to your organisation, there is plenty of information which can be used by the attacker to cause damage to the organisation’s security posture.